-
Learn More
Anatomy of a Ransomware Attack
News Article from Sectigo
 News Article Jul 09, 2019
News Article Jul 09, 2019There have been a few real-world cases where white-hat hackers and researchers have been able – in limited, controlled instances – to penetrate a car’s electronics and communications systems, take over its steering and acceleration systems, and potentially do real damage.
-
Blog Post Jul 07, 2019
Bad Cars: Anatomy of a Ransomware Attack
Suppose cyber hackers successfully penetrated and infected critical components in a manufacturer's vehicles? Imagine now that the bad guys had the software or security keys that could fix these problems, but hold them as ransom, jeopardizing an entire fleet of new cars.
-
Learn More
Wider DevOps Needs Sharper Identity Certificates
News Article from Sectigo
 News Article Jul 05, 2019
News Article Jul 05, 2019Commercial CA provider Sectigo has pointed to a ‘widening world’ of DevOps (where many different platforms are potentially used) and suggests that this helps to validate its position as a provider of automated PKI management software.
-
Learn More
How to Tackle the Tough Stuff Around IoT Security - Part I
News Article from Sectigo
 News Article Jul 02, 2019
News Article Jul 02, 2019Alan Grau, VP of IoT, Embedded Systems (and president & founder of Icon Labs) answers questions about the acquisition, digital certificates, as well as on-premise and cloud-based CAs.
-
Learn More
How to Tackle the Tough Stuff Around IoT Security - Part II
News Article from Sectigo
 News Article Jul 02, 2019
News Article Jul 02, 2019Security has not historically been a core competency of device manufacturers, so the question is, do they learn it and do it themselves or find partnerships with companies like Sectigo? In this Q&A, Sectigo's CTO of IoT, Jason Soroko, discusses the company's acquisition of Icon Labs.
-
Listen Now

EPISODE 25
Broadcast Date:
July 2, 201920 minutes
 Podcast Jul 02, 2019
Podcast Jul 02, 2019Root Causes 25: Entropy and Random Numbers
One cornerstone of successful cryptography is entropy, or the ability to create genuinely unpredictable values. Join our hosts as they discuss.
-
Learn More
How Loss Aversion Ties into Decision Making for EV SSL Certificates
Blog Post from Sectigo
 Blog Post Jul 01, 2019
Blog Post Jul 01, 2019I have been engaged with many decisions makers who are evaluating whether or not to use Extended Validation SSL on their sites, and I have repeatedly observed how a psychological phenomenon called loss aversion biases this decision-making process. Read on to learn more.
-
Learn More
Email Attacks - the Costliest of Cyber Crimes?
News Article from Sectigo
 News Article Jun 28, 2019
News Article Jun 28, 2019Using S/MIME email certificates across an enterprise - an efficient way of digitally signing and encrypting emails - combats spear phishing by enabling the user to confirm the true sender of an email.
-
Learn More
Return of the IoT Botnet: Silex Exposes the Underbelly of IoT Devices
Blog Post from Sectigo
 Blog Post Jun 27, 2019
Blog Post Jun 27, 2019IoT botnets and cyberattacks just keep coming. The most recent attack, the Silex botnet, is particularly nasty. It doesn’t use devices to create DDoS attacks or attempt to steal personal data. The malware simply deletes the software from the device rendering it useless, or “bricking” the device. Fortunately, there are ways to prevent these kinds of attacks.
-
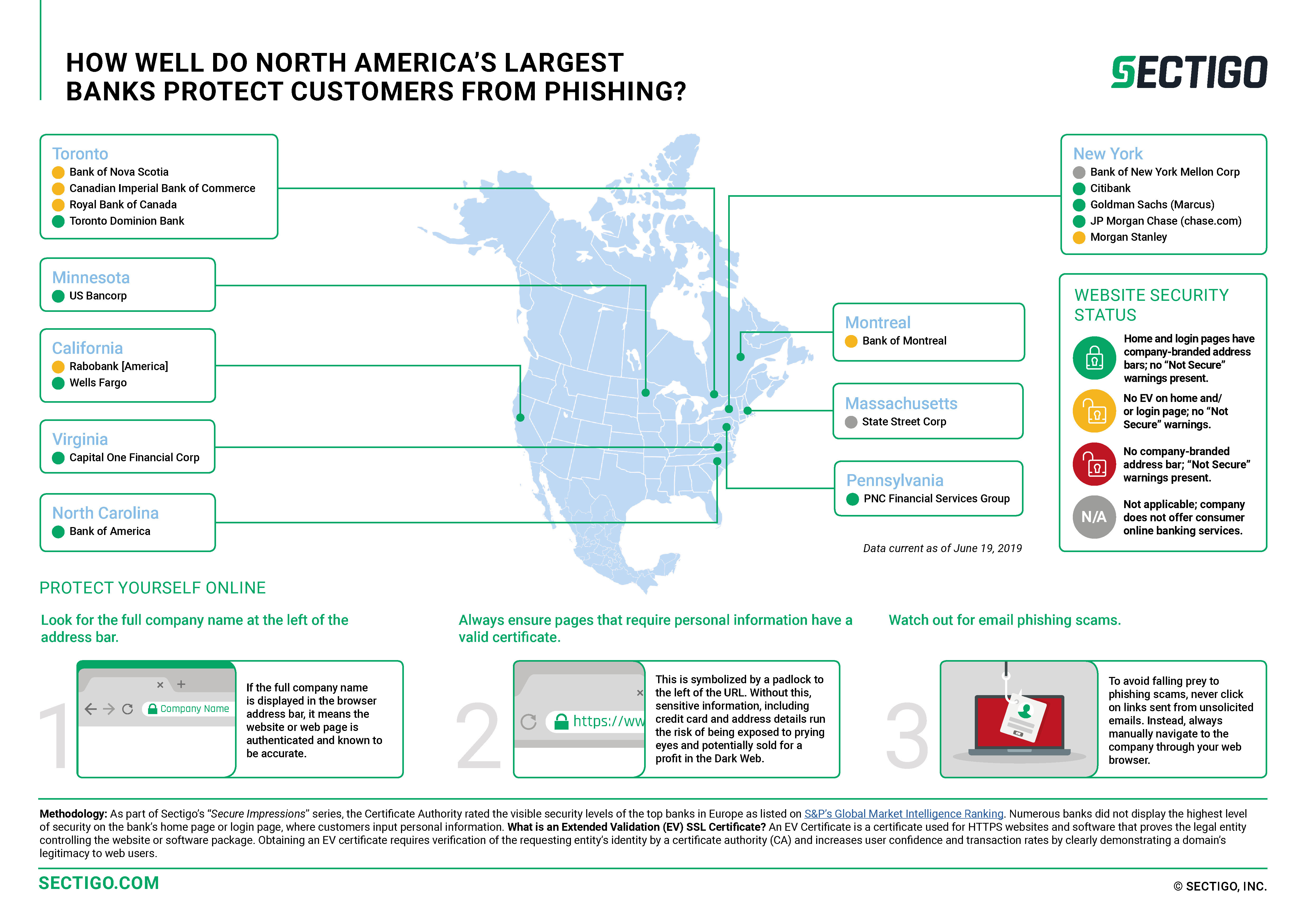
Press Release Jun 27, 2019
40% of Large NA Banks Fail to Use Security Best-Practices Vs. Phishing
Sectigo today released findings from its latest Secure Impressions: Online Banking Study, revealing how well the largest banks in North America and Europe ensure and demonstrate security of customer information on their online banking websites. The study found that a notable percentage of banks left customers vulnerable to phishing scams, but that all banks do use some form of SSL certificates.
-
Listen Now

EPISODE 24
Broadcast Date:
June 27, 201916 minutes
 Podcast Jun 27, 2019
Podcast Jun 27, 2019Root Causes 24: Certificate Revocation
Certificate revocation is an essential part of the certificate lifecycle. Join our hosts as they discuss revocation by the CA, code signing, and malware.
-
Learn More
A Quarter of European Banks Leave Customers Exposed to Phishing Scams
News Article from Sectigo
 News Article Jun 27, 2019
News Article Jun 27, 2019An assessment of the digital certificates used to secure the home and login pages of major banks’ websites was conducted by Sectigo, the world’s largest commercial CA for online security technology.