Definition of malware & the different types that exist
As the personal computer gained popularity – eventually becoming a staple in pretty much every home – cybersecurity risks began to rise. Hackers could gain access to these computer systems and would then overload unsuspecting users’ machines with viruses, bugs, and other damaging programs.
It was during this time that the term “malware” first began to reach household name status. We all know that malware is related to viruses, but what exactly is it? And why do cybercriminals use it so often?
Cybercrime continues to be prolific throughout every corner of the internet. For business owners, the last thing you need while managing your business is to be stuck having to clean up your website’s code because a criminal gained access to your files.
This makes it essential to understand not only what malware is but also the different types and how to get rid of it.
What is malware?
Malware is a term used to cover a broad range of malicious software. In short, malware is software that is intended to infiltrate and harm a device, service, or a network.
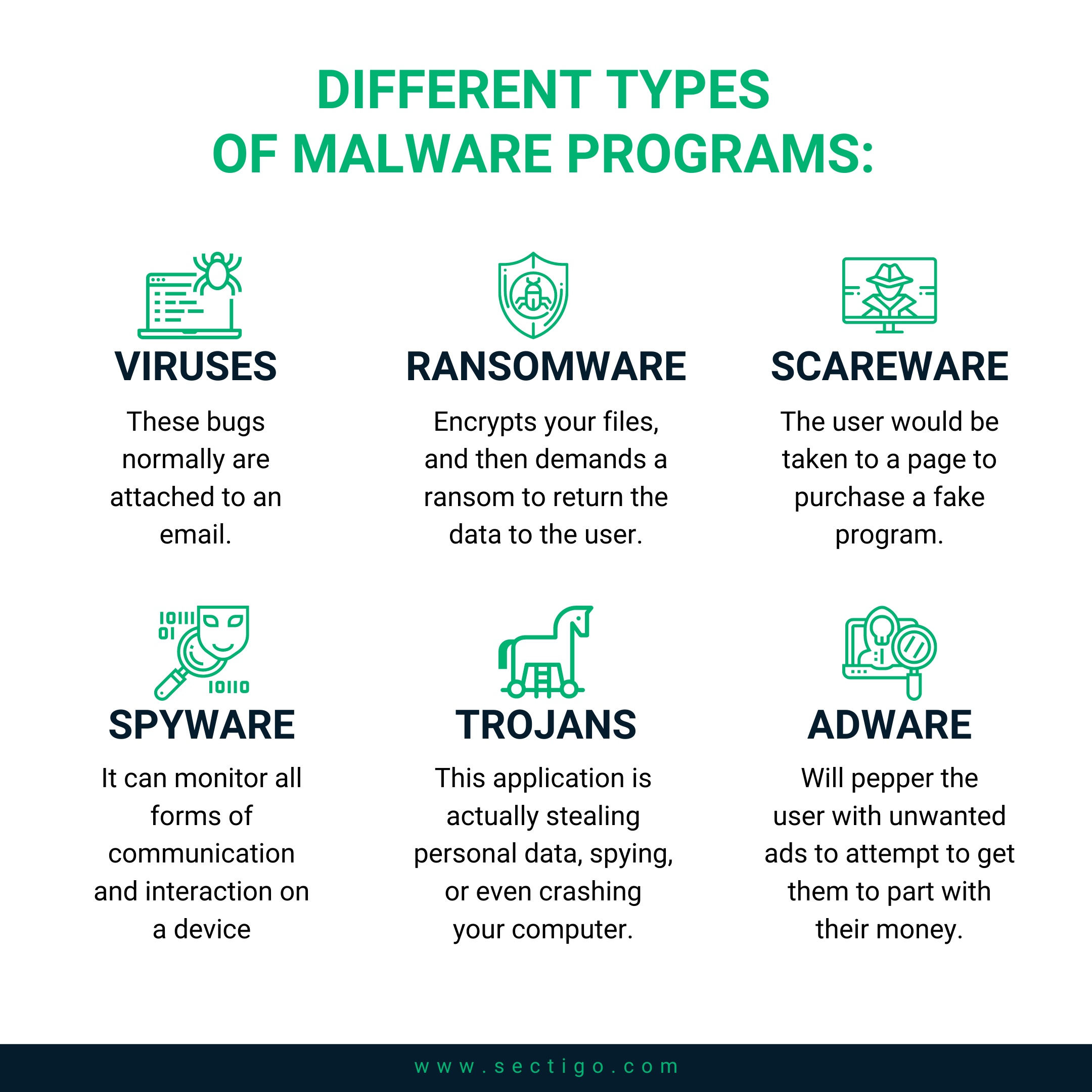
It can take the form of different types of malicious programs, each with their own purpose or intent. The most common types of malware include:
- Viruses. These bugs normally are files attached to an email. An unsuspecting victim opens the email attachment and unleashes the virus on their machine.
- Ransomware. This might be the most popular form of malware among hackers. With ransomware attacks, a program installs itself onto your computer, encrypts (or locks) your files, and then demands a ransom to return the data to the user. This is a very profitable scheme, which is why it is so popular.
- Scareware. You might come across these warnings often: “WARNING: Your computer has been infected with a virus! Click HERE to remove it!” The user would be taken to a page to purchase a fake program. You see these very often on ads and pop-ups, and they are very scary to inexperienced users.
- Spyware. A slightly more sophisticated form of malware, spyware slips onto your machine without your knowledge, then captures and records your browsing habits, including passwords and other personal information, sending that information to the creator of the spyware. Someone running a spyware operation can monitor all forms of communication and interaction on a device.
- Trojans. Another very common form of PC malware, trojan horses are typically set up to appear harmless - or to serve a purpose that a user would want. Trojans are then installed by a user, and it becomes too late to realize that this application is actually stealing sensitive data, spying, or even crashing your computer.
- Adware. Another popular use of malware, adware programs will pepper the user with unwanted advertisements to attempt to get them to part with their money. This was very widespread in the early 2000s, as it was a lucrative way to spread malware.
There are many, many other forms of malware, but these are the most common. Because there are so many ways to sneak malware onto someone’s computer or phone, hackers are typically able to stay ahead of many users’ efforts to avoid them. Even a “smart” internet user can allow themself to be infected unwittingly.

What can happen?
Malware attacks can lead to many different results and issues.
One possible outcome is cybercriminals stealing sensitive information and data for their own nefarious purposes. One of the more popular forms of this would be to steal a person’s identity. Identity theft continues to be a problem worldwide, and malware is typically the culprit. This malicious software can record personal data, such as addresses, phone numbers, and social security numbers, so that identities can be stolen rather easily.
The same is true of financial data. Once bank accounts or credit card numbers are logged by a piece of malware, it is not difficult to rack up thousands of dollars’ worth of purchases on someone else’s accounts.
Another use of malware would be to take control of a user’s computer. This is handy when a hacker is looking to launch a DDoS (distributed denial of service) cyberattack on another network. By taking control of multiple computers, the hacker can create a “botnet,” which is used to repeatedly make connection attempts to a server, thus crashing the servers.
Finally, one of the more recent uses of malware is to mine cryptocurrencies such as Bitcoin. Mining these currencies can be very profitable, but it takes a lot of computing power to do so. Hackers can multiply their efforts by forcing other people’s machines to do the mining for them.
If you are a website owner, the last thing you want to be is an accomplice for malware attacks. These attacks, if left unaddressed for too long, can cause distrust amongst customers, kill your revenues, and even damage your online reputation.
How to get rid of malware
In your efforts to build a trusted business, you may wind up being the victim of a website attack. It happens to thousands of businesses every day. There are certain warning signs to watch for that may indicate your site has been infected.
Be aware of the following signs of malware:
- A defaced website
- Odd code displayed at the bottom of your page
- Severely crippled website performance or site speed
- A significant decrease in site traffic
- A red warning page being displayed when trying to access your site
Being the victim of malware can have disastrous consequences for your company. If you notice any of the signs above, it’s time to act fast to get rid of it before its impact is magnified.
Option 1: the manual way
If you consider yourself to be tech-savvy, then you may be able to pull out that malicious code yourself. It takes time and resources, but it can be done:
- Find the source of the malware. This is done through what is called a “local file search.” It’s the easiest and fastest way to sift through all the files on your website. You do this by downloading all your website files to your computer. This way, you can look at recently modified files and search within the files for the changed code.
- Search for the right clues. There are some signs that malware has been added to your website’s code. Often, hackers will use particular PHP codes, such as eval, base64_decode, fromCharCode, gzinflate, shell_exec, globals, and error_reporting(). Obviously there are many others, but these are the most common used by cybercriminals today.
- Delete the malware. Once you find the malicious code, remove it. It may even be best to find a fresh copy of the file in question and overwrite the edited copy. Either way, removing the edited copy will remove the malware from your site.
If this approach sounds too involved, there’s another option.
Option 2: the automatic way
Cybersecurity tools can automatically detect infections on your website and clean them up as quickly as possible. A tool like this can be used to prevent an attack or can be added to a site to help with clean-up quickly after signs of malware are noticed.
SiteLock, a Sectigo company, has a tool that will automatically keep an eye on your site and catch malware threats before they run out of control. The site will be scanned daily, and if threats are detected, infections can be neutralized and removed while your site continues to run.
This tool does more than just scan for malware infections, though: it also proactively scans for the potential for infections. This means it pinpoints vulnerabilities in your system that could be an open window for hackers to get through. Depending on your plan, the software can even patch these vulnerabilities so they are no longer opening up your business to unneeded risk, which can deliver peace of mind.
Proactivity is Key
It’s extremely important to be proactive in keeping your business website out of the hands of hackers. Protect your site and your users with a tool that automatically detects cyberthreats and provides a fix for them. Contact our team at Sectigo to learn more.
