Social Engineering: Friend or Foe?
In a social engineering attack, a bad actor uses human interaction (social skills) to acquire information about a company and/or its computer systems. Attackers often seem unassuming and respectable, often claiming to be a new employee, a service technician, or a member of the service-providing company and may even offer credentials to support that identity.

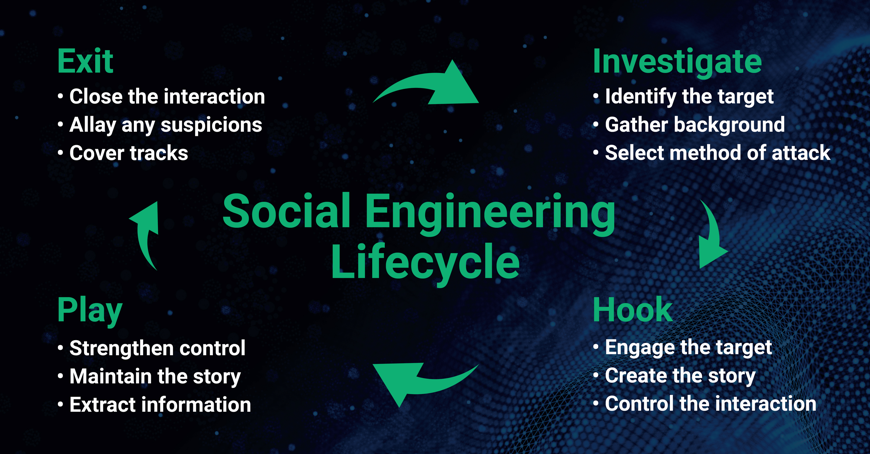
Understanding elements in the social engineering attack lifecycle helps users prevent attacks.
If an attacker is not able to gather enough information from one source, he or she may contact another source within the same organization and utilize the information from the first source to establish credibility and continue to gather information to build an attack.
To combat social engineering:
- Be suspicious of people you don’t recognize and question their presence within office locations.
- Be suspicious of unsolicited phone calls, visits, or email messages from individuals asking about employees or other internal information. If an unknown individual claims to be from a legitimate organization, try to verify his or her identity independently.
- Do not provide personal information or information about your organization, including its structure, systems or networks, unless you are certain of a person's authority to have that information.
Earlier this year, Infosec Institute published several of the Most Common Social Engineering Attacks, including web server attacks, phishing (and whaling), pretexting, and more. This resource sheds light on the tactics that attackers use to trick users into sharing sensitive information.
If you think you might have revealed sensitive information about yourself to a “foe,” it is important to contact your local authorities and file a report. Change passwords that may have been compromised and monitor accounts for any sign of identity theft. If you think you might have revealed sensitive information about your organization, report it your supervisor, as well as advise the appropriate personnel responsible for IT Security and Data Protection.
