Six Steps for Migrating PKI Based Cybersecurity Systems to Quantum-Safe Cryptography
PKI is used in a wide range of systems, including online shopping, credit card transactions, validating passports and ID badge systems, and even for managing the control systems that power the electric grid. Ensuring PKI solutions can provide adequate protection for these systems in the face of quantum computing attacks is critical.
The rapid development of quantum computers will deliver powerful computing capabilities that solve a wide range of computing problems that are simply intractable with traditional computers.
Unfortunately, one of the consequences of quantum computers is that it will be easier for hackers to break some of today’s widely used encryption algorithms. Specifically, we are referring to the RSA and ECC encryption algorithms that are fundamental to the existing PKI (public key infrastructure) systems that underpin most modern security, communication, and identification solutions.
PKI is used in a wide range of systems, including online shopping, credit card transactions, validating passports and ID badge systems, and even for managing the control systems that power the electric grid. Ensuring PKI solutions can provide adequate protection for these systems in the face of quantum computing attacks is critical.
Researchers predict that quantum computers will render current ECC and RSA encryption obsolete somewhere around 2026-2031. This means that we have roughly 5-to-10 years to migrate to new, quantum-safe encryption algorithms, and even less time to implement long-term protections for data that is being generated today that needs to remain secret for many years into the future.
Phased migration to quantum-safe cryptography
Migrating to quantum-safe crypto algorithms requires planning and updates to multiple systems. Typically, this includes both internal systems developed by the company, as well as third-party applications, servers, and systems.
Businesses must begin planning now to take preventative measures to migrate to quantum-safe crypto. For enterprises of any size, these measures will be a major undertaking. Fortunately, all systems do not have to be updated simultaneously.
By using “hybrid certificates,” that is certificates with both traditional RSA or ECC keys and new quantum-safe keys, organizations can undertake a gradual-yet-safe migration. Hybrid certificates allow devices that do not yet support quantum-safe crypto to simultaneously work with new systems that support quantum safe crypto, thereby enabling a gradual migration of systems to quantum-safe crypto.
More details about hybrid certificates can be found here.
Once all systems are upgraded to support quantum-safe crypto, the hybrid certs can be dropped in favor of pure quantum-safe certificates, completing the migration. In contrast, some companies may choose to move directly from traditional crypto to quantum safe crypto without a transition period using hybrid certs. For environments in which all systems can be upgraded simultaneously, the transition period with hybrid certs can be skipped. As the goal is to move all systems to using pure quantum-safe certs, moving directly to quantum-safe certs will achieve this goal more quickly. However, direct migration introduces risk. If any system is not properly updated, it will no longer be able to communicate with other systems.
The following steps are required for either direct or hybrid migration plans.
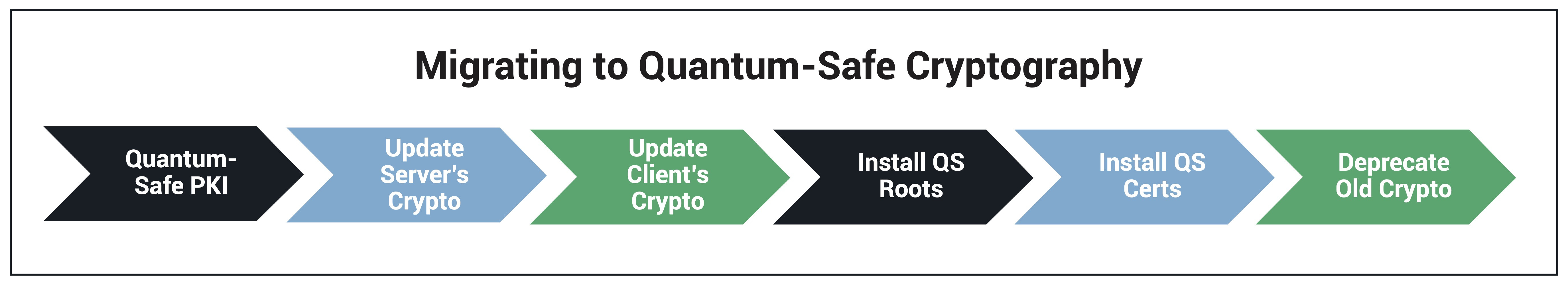
There are six steps required for an organization to successfully migrate to quantum-safe cryptography—whether upgrading directly or using hybrid certificates.
Migrate to quantum-safe PKI
The first step towards migrating to quantum-safe cryptography is to upgrade the PKI infrastructure, including the certificate authority, to utilize quantum-safe crypto algorithms. Rather than trying to upgrade internal PKI systems, this may be an ideal time for companies to migrate to a commercial CA, such as Sectigo, which can provide commercial support for quantum-safe crypto algorithms.
Whether using an in-house PKI system or a solution from a commercial vendor, it is critical that the CA provide support for quantum-safe crypto algorithms and quantum-safe certificate issuance. If the IT security team chooses to use hybrid certificates, they must select a CA that supports both hybrid certificates and quantum-safe certificates.
Once an organization upgrades their existing CA, or selects a new CA, the CA must issue a new quantum-safe root and intermediate certificate.
Update server crypto algorithms
Migrating to quantum-safe crypto requires updating the crypto libraries used by server applications to support both the new crypto algorithms and the new quantum-safe certificate formats, including hybrid certs, if used. If hybrid certificates are used, server applications will need to recognize and process both traditional RSA/ECC certs and hybrid certs containing quantum-safe crypto keys. This requires the server applications to distinguish between the two different certificate types and handle each with the proper crypto algorithm for that certificate type.
Update client crypto algorithms
Teams will also need to update client applications to use quantum-safe crypto algorithms. Once fully upgraded, administrators can discontinue use of traditional RSA/ECC keys/certificates in client applications and instead use the new quantum-safe equivalents.
The exception to this policy is a client application that communicates with multiple server applications that may not all simultaneously be upgraded to quantum-safe crypto. In this case, hybrid certificates will allow the client to work with servers supporting traditional RSA/ECC crypto, while using quantum-safe algorithms with servers that support these newer algorithms.
Install quantum-safe roots on all systems
Each system utilizing PKI has a trusted root store. This root store contains the certificates for the root and intermediate CAs that issue certificates within the PKI system. Once systems have been updated to support quantum-safe crypto algorithms, these root stores must be updated to add the new root and intermediate certificates.
Issue and install quantum-safe certs for all devices/applications
After IT teams have updated all of a company’s systems to support quantum safe crypto, they must issue new certificates and install them on all the endpoints. Once completed, each device can begin using quantum-safe crypto algorithms, as enabled by the new certificates.
Deprecate traditional encryption algorithms/revoke RSA/ECC certs
The final step in migrating to quantum-safe crypto is to deprecate the traditional encryption algorithms so they are no longer used. This can be done gradually on applications and systems as they are migrated to the new algorithms. After all systems have been migrated, the root ECC and RSA certificates should be revoked, ensuring they are not used by any systems.
Automated Certificate Management
Migrating to new crypto algorithms and PKI systems will require issuing large numbers of new certificates as each device/application will require a new certificate. For organizations that do not already support automated certificate management, this is excellent time to consider implementing automation tools.
There are tools available today that both enable automated certificate discovery and renewal to ensure systems do not fail due to expired certificate, as well as ease the administrative burden of installing new certificates on devices and systems. Support for automation tools should be a high priority for security teams considering a new PKI vendor.
Summary
Quantum computers capable of breaking traditional crypto algorithms will arrive within the next five to ten years. For most organizations, the task of migrating to new, quantum-safe crypto algorithms will require a major, well-planned effort spanning internal development teams and third-party vendors. Companies will have to upgrade the PKI systems that they are using along with the applications using these certificates.
Hybrid certificates enable a gradual migration of systems, but ultimately all systems using ECC or RSA encryption must migrate to new, quantum safe-crypto algorithms. Otherwise, an organization’s applications and systems will be vulnerable to attacks using quantum computers.
