What is SCEP (Simple Certificate Enrollment Protocol)?
SCEP (Simple Certificate Enrollment Protocol) automates PKI certificate issuance by streamlining the process of communicating with a Certificate Authority (CA). It enables secure, efficient certificate management for devices and servers by using a URL and a shared secret for authentication, minimizing manual errors. Widely supported across systems like Microsoft Intune and Apple MDM, SCEP is pivotal for managing mobile devices, routers, and enterprise applications, ensuring secure connections. Its automation reduces the complexity of manual certificate management, mitigates risks of expiration or breaches, and supports large-scale deployments through tools like Sectigo Certificate Manager.
Table of Contents
What is SCEP (Simple Certificate Enrollment Protocol)?
SCEP stands for Simple Certificate Enrollment Protocol and is a certificate management protocol that helps IT administrators issue certificates automatically. Public key infrastructure (PKI) certificate issuance requires a process for exchanging information with a trusted Certificate Authority (CA) like Sectigo so that the CA can authenticate that a certificate user legitimately represents the identities and domain name(s) associated with the PKI certificate before issuance is completed. SCEP standardizes that exchange with the CA using a URL and a shared secret, making it faster and easier for IT teams to enroll certificates on devices than communicating this information manually.
SCEP has been around for a long time and has gained significant traction with businesses. As the SCEP protocol has no licensing fees and requires very little time for IT teams to configure and execute, it has become an almost ubiquitous component of enterprise security.
For what use cases is it most used?
SCEP is commonly applied to a number of certificate use cases. Notably, Mobile Device Management (MDM) systems like Microsoft Intune and Apple MDM use SCEP for PKI certificate enrollment on the growing number of mobile devices and smartphones used by business employees. This allows mobile devices to authenticate connections between apps and enterprise systems and resources. Most networking gear, including routers, load balancers, Wi-Fi hubs, VPN devices, and firewalls, also support the SCEP protocol for certificate enrollment.
SCEP Automates PKI Certificate Enrollment for Mobile Devices and Smartphones via Mobile Device Management (MDM) Systems for Secure Connections to VPN, WI-Fi, and Enterprise Applications
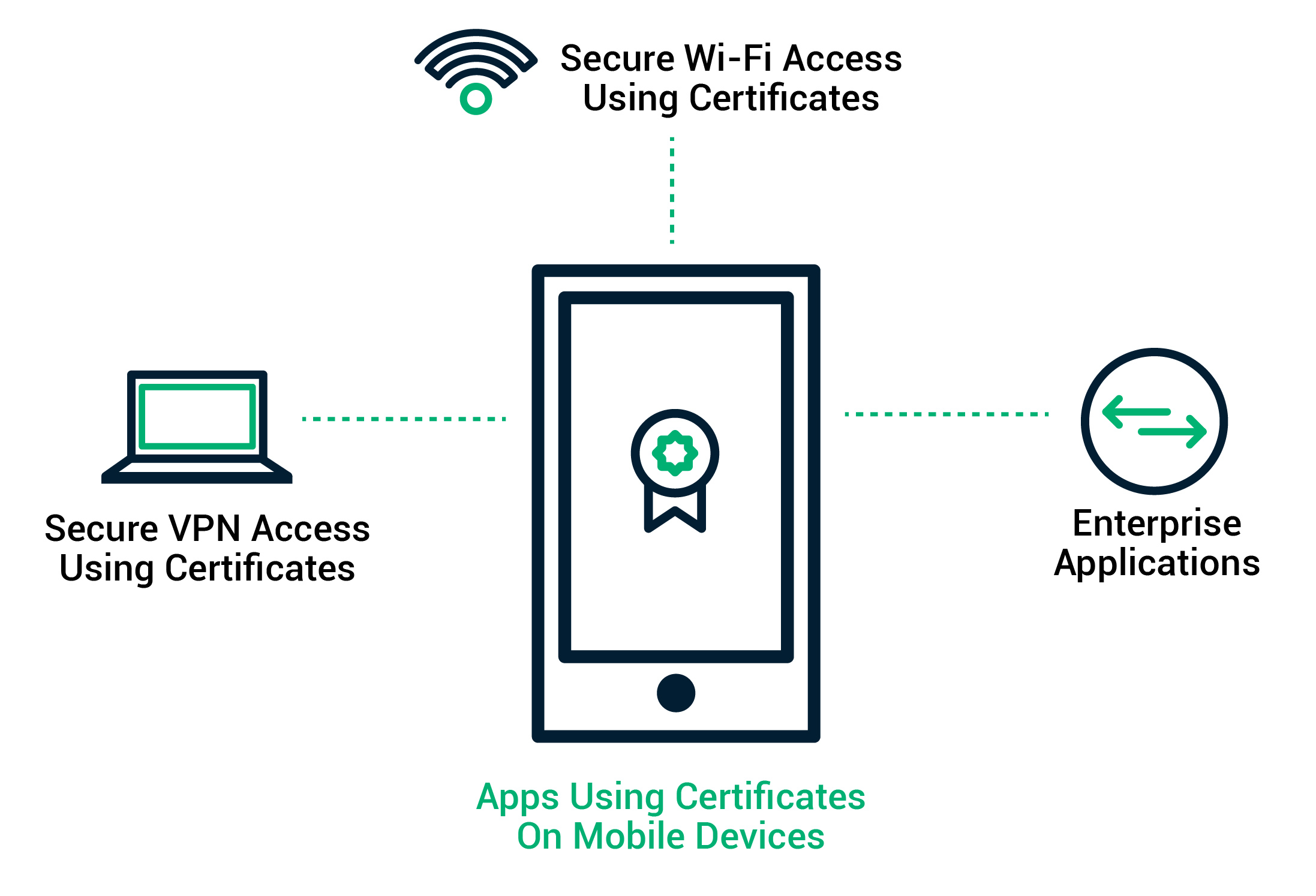
This protocol is supported on the most common server and device operating systems, including Microsoft Windows, Linux, and Apple iOS and MacOS, as well as directory systems like Active Directory. You can leverage Sectigo’s SCEP server to manage your certificates across all of the device use cases and OS and directory environments you may use in your organization.
Why use SCEP?
While public key infrastructure offers the strongest and easiest authentication and cryptographic solution for digital identity, the complexity and scale of certificate deployment for most enterprises can be a challenge for busy IT teams. Manually deploying and managing certificates is time-consuming and prone to errors. The end-to-end process of certificate issuance, configuration, and deployment can take up to several hours, whether an enterprise is deploying a single certificate for a Wi-Fi router or managing millions of certificates across all networked devices and user identities it supports. As a result, businesses are exposed to unnecessary risk of sudden outages or failure of critical business systems along with breaches and Man-in-the-Middle (MITM) attacks.
Additionally, manual certificate management puts enterprises at significant risk as it increases the likelihood that certificates can be forgotten until expiration or gaps in ownership occur. With the many potential pitfalls inherent in managing PKI certificates manually, enterprises need the automated certificate enrollment standard the Simple Certificate Enrollment Protocol provides to ensure certificates are correctly issued and configured on a large quantity of devices without human intervention. This automation helps reduce risk and allows IT departments to control operational costs.
How does the SCEP protocol work?
The SCEP enrollment process standardizes the information exchange with the Certificate Authority required to authenticate the certificate request and to issue the certificate. The key elements of this process are:
- SCEP URL: The URL instructs where devices communicate with the CA to enroll the client certificate. This URL can be placed in an MDM to automate certificate enrollment on mobile devices at scale.
- SCEP Shared Secret: A Shared Secret is a case-sensitive entrusted password exchanged between the SCEP server and the CA used to authenticate that a user legitimately represents the identities and domain name(s) associated with the PKI certificate.
- SCEP Certificate Signing Request: Once the connection between the SCEP server and the CA is established and the Shared Secret is authenticated, the Certificate Signing Request (CSR), or SCEP request, can be submitted to the CA. This CSR includes the configuration profile that allows managed devices to auto-enroll for certificates.
- SCEP Certificate Configuration Profile: Certificate management platforms and MDMs often have a specific set of configuration parameters that are used to define the certificate profile, including certificate validity period, key size, SCEP configuration name, Subject Alternative Name type and value, number of failed attempt retries and retry interval, and additional challenge password type and value.
- SCEP Signing Certificate: To ensure valid certificates are used, most MDMs require a signing certificate that has been signed by the CA to also be used by devices. This signing certificate encapsulates the entire certificate chain, including the signing certificate, Intermediate CA, and Root CA.
SCEP enrollment process steps
Here are the SCEP enrollment process steps to establish automatic certificate enrollment for a typical certificate management platform or MDM:
- Add the SCEP URL
- Add the SCEP Shared Secret
- Upload the SCEP Signing Certificate
- Define the SCEP Configuration that is sent to devices
- Define any application-specific certificate settings (e.g. for Wi-Fi or VPN)
- Specify which devices receive certificates
Then once authenticated by the CA, a signed CA certificate will be deployed onto the device.
SCEP certificate configuration profile
When setting up a SCEP server, there are a number of certificate properties that the administrator can set in the certificate configuration profile to customize the SCEP implementation. These include things like the following:
- Certificate template name
- Certificate type (whether it will be deployed to a device or an end user)
- Subject name format (how the server creates the certificate request subject name, for example using an email address in the case of a user or a server name or IP address in the case of a device)
- The certificate validity period (specifying the amount of time required before certificate expiration or certificate revocation)
- Hash algorithm
- Root CA certificate
- Key usage. Key usage can include key encipherment (allowing key exchange when a key is encrypted), or digital signature (allowing exchange when the key is protected by a digital signature).
How does Sectigo support this protocol?
Sectigo recognizes the complexity and scale of most enterprise certificate needs. Enterprises rely on PKI certificates to authenticate and encrypt everything from web servers both in the cloud and on-premises, networked devices, mobile devices, user identities, email systems, network appliances, IoT devices, DevOps environments, digital signatures, and more. As Sectigo offers device certificates that support SCEP in addition to SSL/TLS certificates, Code Signing, S/MIME, and other X.509 certificates that protect critical business systems, enterprises also need a way to automate the end-to-end certificate lifecycle management at scale. Sectigo Certificate Manager supports the SCEP protocol to deliver automated certificate lifecycle management.
How to configure SCEP in Sectigo Certificate Manager
Sectigo Certificate Manager (SCM) provides a single-pane-of-glass management interface that seamlessly integrates enterprise device architectures like Microsoft Intune and Apple MDM, speeding and simplifying the discovery, issuance, deployment, and renewal of all certificates. Sectigo Certificate Manager allows you to issue device certificates using SCEP by creating configuration profiles which are pushed to target devices. The configuration profile can be created using software such as the Apple iOS configuration utility.
To issue device certificates through SCEP, you create new device certificate profiles and enable them for SCEP enrollment. Each device certificate profile is assigned with a device Profile ID to identify it when applied to the devices.
The process must meet these prerequisites to succeed:
- Your Sectigo account must have at least one certificate profile configured for use with device certificates.
- SCEP enrollment needs to be enabled for an organization or department, and an access code must be specified. This can be done when adding or editing an organization or department.
How to issue certificates via Sectigo Certificate Manager using SCEP – Simple Certificate Enrollment Protocol
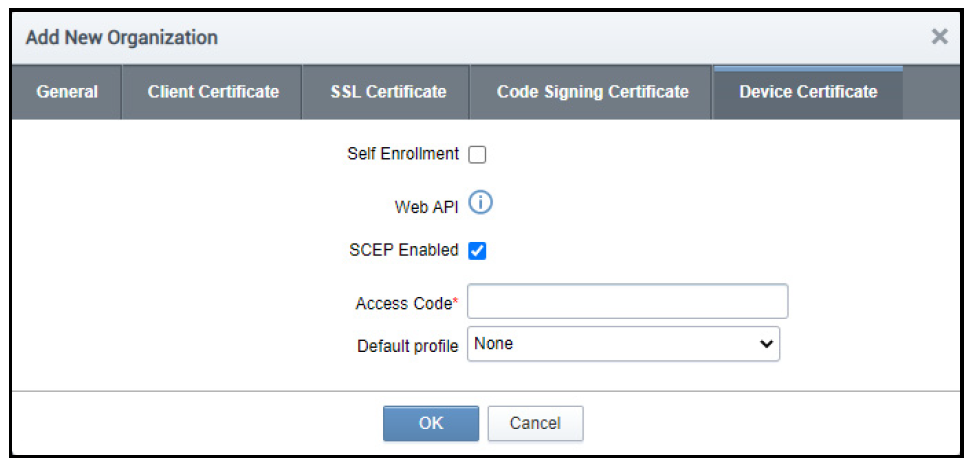
Typically, the process involves the following:
- You generate a configuration profile for OTA enrollment using configuration software, then apply the profile to target devices. The SCEP enrollment access code specified for the organization or department is included in the profile. This means the certificate request generated by the device contains the same access code as the challengePassword parameter.
- Once applied, the device generates the certificate request and forwards it to Sectigo Certificate Manager.
- The certificate requests are added to the Device Certificates area for approval. The status of the certificate is indicated as Requested.
- An RAO or DRAO with appropriate privileges approves the request, and then SCM forwards the request to Sectigo. The status of the certificate changes to Applied. Upon issuance of the certificate, SCM collects the certificates. The status of the certificate changes to Issued.
- The SCEP server pushes the certificates to the target devices for installation.
For a complete guide to SCEP configuration using Sectigo Certificate Manager, go to the Sectigo Knowledge Base and refer to the Sectigo Certificate Manager Administration Guides.
For details on values of parameters to be specified in the configuration profile, contact us
