Quantum Cryptography & Encryption: What It Is & How It Works


What Is Quantum Cryptography?
Quantum cryptography is a science that applies quantum mechanics principles to data encryption and data transmission so that data cannot be accessed by hackers – even by those malicious actors that have quantum computing of their own. The broader application of quantum cryptography also includes the creation and execution of various cryptographic tasks using the unique capabilities and power of quantum computers. Theoretically, this type of computer can aid the development of new, stronger, more efficient encryption systems that are impossible using existing, traditional computing and communication architectures.
While many areas of this science are conceptual rather than a reality today, several important applications where encryption systems intersect with quantum computing are essential to the immediate future of cybersecurity. Two popular, yet distinctly different cryptographic applications that are under development using quantum properties include:
- Quantum-safe cryptography: The development of cryptographic algorithms, also known as post-quantum cryptography, that are secure against an attack by a quantum computer and used in generating quantum-safe certificates.
- Quantum key distribution: The process of using quantum communication to establish a shared key between two trusted parties so that an untrusted eavesdropper cannot learn anything about that key.
This article focuses on post-quantum cryptography, quantum-safe certificates, and how enterprises can protect themselves as these risks become a reality.
Why Is This Science Needed?
The rapid development of quantum computers promises to deliver powerful computer science capabilities that solve a wide range of critical, even lifesaving, computing problems that traditional computers simply cannot. Unfortunately, they are also capable of generating new threats at unprecedented speed and scale. For example, complex mathematical equations that take traditional computers months or even years to solve can be broken in moments by quantum computers running quantum algorithms like Shor’s algorithm. As a result, systems capable of breaking traditional math-based cryptographic algorithms are predicted to arrive within the next 5-10 years.
Hackers who apply this type of computing to their arsenal of attacks will be able to quickly break encryption algorithms widely used today. Specifically, the RSA and ECC encryption algorithms, which are fundamental to public-key cryptography and symmetric key cryptography, are mathematical equations that can be solved quickly by these computers. This compromises most modern cybersecurity, communication, and digital identities.
Ensuring PKI solutions can provide adequate protection for these systems and data against quantum computing attacks is essential. This means that new quantum-safe algorithms must be developed and that businesses must migrate to new, quantum-safe certificates. The task of migrating to new digital certificates requires a well-planned effort to upgrade PKI systems and the applications using these certificates.
Development of and migration to quantum-safe certificates must take place as soon as possible and cannot wait until RSA and ECC algorithms are broken. Hackers today can steal sensitive data that is encrypted using current algorithms and then decrypt it later when the quantum computers are available. Businesses need to address this threat now so that their organizations’ data, applications, and IT infrastructures remain protected for many years into the future.
How Does Quantum-Safe Cryptography Work?
Academic, technology, and public sector organizations worldwide have accelerated efforts to discover, develop, and implement new quantum-safe cryptographic algorithms. The objective is to create one or more algorithms that can be reliably resistant to quantum computing. The task is technically difficult, but not impossible.
Good cryptosystems require a tough problem to solve. Quantum encryption comes from choosing a mathematical approach that is difficult for any computer to solve. Current RSA and ECC cryptographic algorithms are based on algebraic problems using very long random numbers. These are then applied to both public keys and private keys in a way that the private key, which is the secret key, cannot be derived from the public key through brute force attacks in a reasonable amount of time using traditional computing. Attacks are rendered ineffective because they are too computationally expensive. With quantum computing, these fundamental underlying assumptions, upon which our entire security architecture is built, are no longer true. The new computers can derive the private key from a public key in a reasonable amount of time.
Quantum cryptography works by solving entirely different problems. For example, lattice-based cryptography is based on a geometric approach rather than an algebraic one, rendering a quantum computer’s special properties less effective at breaking quantum encryption systems. This type of cryptography is tough for both classical computers and quantum ones to solve, making it a good candidate to be the basis of approach for a post-quantum cryptographic algorithm. Quantum-safe algorithms have been proposed and are currently undergoing a selection process by the National Institute of Standards and Technology (NIST), the U.S. federal agency that supports the development of new standards, with plans to release the initial standard for quantum-resistant cryptography in 2022.
How Is Quantum Key Distribution Different?
Quantum key distribution (QKD) uses the principles of quantum mechanics to send secure communications by allowing users to safely distribute keys to each other and enabling encrypted communication that cannot be decrypted by eavesdropping malicious actors. QKD secures communications but does not encrypt the data being communicated like quantum-safe certificates do.
QKD systems establish a shared private key between two connected parties and use a series of photons (light particles) to transmit the data and key over optical fiber cable. The key exchange works based on the Heisenberg uncertainty principle, namely, that photons are generated randomly in one of two polarized quantum states and that the quantum property of a photon cannot be measured without altering the quantum information itself.
In this way the two connected endpoints of a communication can verify the shared private key and that the key is safe to use, as long as the photons are unaltered. If a malicious actor accesses or intercepts a message, the act of trying to learn about the key information alters the quantum property of the photons. The changed state of even a single photon is detected, and the parties know the message has been compromised and is not to be trusted.
Types of Quantum-Safe Certificates
As quantum-safe cryptography develops, enterprises must now consider what certificates they will implement.
Traditional PKI certificates are today’s gold standard for the authentication and encryption of digital identities. These certificates are referred to as “traditional” because they utilize existing ECC or RSA encryption algorithms. The majority of PKI systems will continue to use traditional PKI certificates for some time to come. They provide effective protection against existing computing attacks, but in the future, they will be made obsolete by quantum computers and attacks on ECC and RSA encryption.
There are three types of digital certificates that are relevant when looking for quantum-safe options. Each type is still adherent to X.509 digital certificate standards that are fundamental to public key cryptography. These types vary distinctly according to their purpose and the encryption algorithm used to create the certificate.
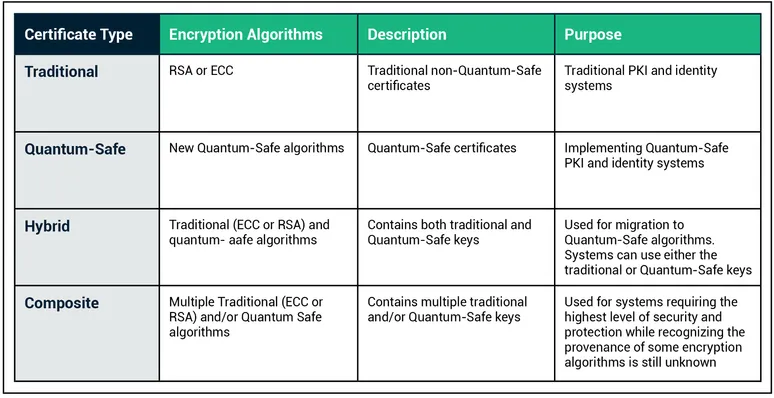
Quantum-Safe Certificates
Quantum-safe certificates are X.509 certificates that use quantum-safe encryption algorithms. While NIST is still in the process of standardizing the encryption algorithms, it has identified a number of candidate algorithms, and implementations of these algorithms are currently available.
Hybrid Certificates
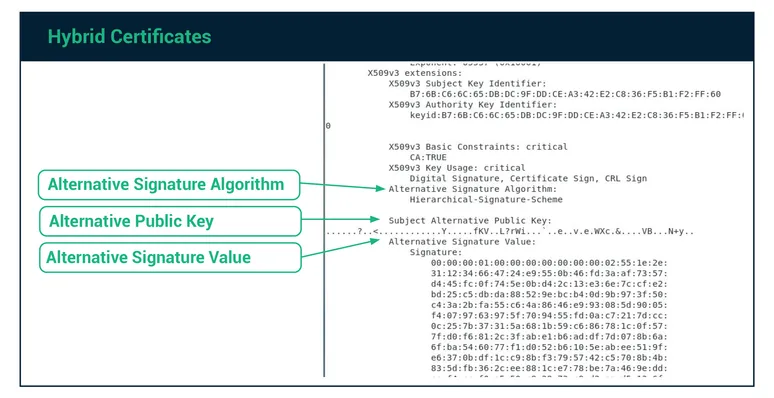
Hybrid certificates are cross-signed certificates containing both a traditional (RSA or ECC) key and signature, and a quantum-safe key and signature. Hybrid certificates enable a migration path for systems with multiple components that cannot all be upgraded or replaced at the same time. This type enables a gradual migration of systems, but eventually all systems using ECC or RSA encryption must migrate to new, quantum-safe cryptographic algorithms.
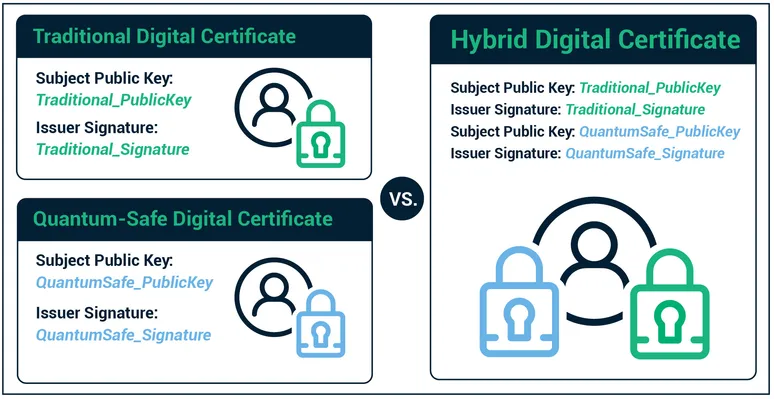
Organizations will need to update the main pieces of their IT infrastructure to utilize quantum-safe cryptosystems and hybrid certificates. As other systems and devices access the newly updated system, they can continue to utilize classic encryption algorithms. The quantum-safe key and signature are stored as an alternative signature algorithm and alternative key. Applications that do not utilize the quantum-safe fields in the hybrid certificates will ignore these additional fields. Over time, security teams can update applications and systems to use the new algorithms. Once the transition is complete, they can deprecate hybrid certificates, and replace them with pure quantum-safe certificates.
Composite Quantum-Safe Certificates
Composite certificates are similar to hybrid certificates in that they contain multiple keys and signatures, but differ in that they use a combination of existing and quantum-safe encryption algorithms. Composite certificates are analogous to having a single door with multiple locks. A person must have all of the keys to all of the locks in order to open the door. The goal of composite keys is to address the concern that any single encryption algorithm, whether currently available or in the future, may be broken using quantum computers. If one of the encryption algorithms proves to have an exploitable vulnerability, the entire system is still secure.
While NIST is coordinating a process to vet and select quantum-safe cryptographic algorithms, these new ones have not yet been thoroughly battle hardened. It is possible that security researchers or hackers could discover vulnerabilities in one or more of these proposed algorithms at some point. Composite certificates provide a strong defense against that risk, making them ideal for protecting environments with high security requirements. However, creating multiple encryption keys and then combining them to issue a composite certificate requires exceptional computational power.
How to Migrate to Quantum-Safe Certificates
Organizations must plan now to take preventative measures against the threats posed by quantum computing. Migrating certificates requires extensive updates to multiple systems, including internal applications, servers, and systems within direct organizational control, as well as connections to external, third-party systems. For enterprises of any size, these measures require significant IT resources, human capital, and time.
The objective is to move all systems to pure quantum-safe certificates as soon as possible. While moving directly to this in one large project may achieve this goal more quickly in theory, direct migration introduces risk. If any single system is not properly updated, it will no longer be able to communicate with other systems and could cause disruption to critical business applications. Additionally, all systems and environments may not be ready from a technical perspective to use quantum cryptographic algorithms at the same time. In that situation, an organization must wait to start their migration process until its entire environment is ready and is exposed to quantum computing attacks in the meantime.
In reality, all systems do not have to be updated simultaneously. A phased approach using hybrid certificates allows organizations to undertake a gradual migration that can start today and requires less risky processes while environments remain safe. Hybrid certificates allow systems that do not yet support quantum-safe cryptography to simultaneously work with new systems that do. Once all systems can support quantum-safe cryptography, the hybrid certificates can be dropped in favor of entirely quantum-safe certificates.
There are six steps required for an organization to successfully migrate, whether upgrading directly or using hybrid certificates.

- Step 1: Migrate to quantum-safe PKI infrastructure - The first step to migrating is to upgrade an organization’s PKI infrastructure, including the certificate authority (CA), to support quantum-safe algorithms. Rather than trying to upgrade internal PKI systems by themselves, IT security teams may look to a commercial CA, such as Sectigo, which can provide commercial support for issuing and managing certificates. Once an organization upgrades its existing CA, or selects a new CA, the certificate authority must issue a new quantum-safe root and intermediate certificate.
- Step 2: Update server cryptographic algorithms - Next, cryptographic libraries used by server applications must be updated to support both the new cryptographic algorithms and the new quantum-safe certificate formats. If hybrid certificates are used, server applications must recognize and process both traditional RSA or ECC certificates and hybrid certificates containing quantum-safe cryptographic keys. This requires the server applications to distinguish between the two different certificate types and properly use both types with the correct algorithmic method for the associated certificate type.
- Step 3: Update client cryptographic algorithms - Teams then can update client applications. Be aware that a client application may communicate with multiple server applications, including external environments, and one or more of those server applications may have not been upgraded yet. In this case, hybrid certificates allow the client to work with servers supporting traditional RSA and ECC algorithms, while using quantum-safe algorithms with servers that support these newer algorithms.
- Step 4: Install quantum-safe roots on all systems - Each system utilizing PKI has a trusted root store. This root store contains the certificates for the root and intermediate CAs that issue certificates within the PKI system. Once both client and server systems have been updated to support quantum-safe algorithms, these root stores must be updated to add the new root and intermediate certificates.
- Step 5: Issue and install quantum-safe certs for all devices/applications - After IT teams have updated all of a company’s systems to support quantum-safe cryptography, they must issue new certificates and install them on all the endpoints. Once completed, each device is protected by the new certificates.
- Step 6: Deprecate traditional encryption algorithms and revoke RSA/ECC-based certificates - The final migration step is to deprecate the traditional RSA and ECC encryption algorithms. This can be done gradually on applications and systems as they are migrated to the new algorithms. After all systems have been migrated, the root RSA and ECC certificates should be revoked, ensuring they are not used by any systems.
Automate Quantum-Safe Certificate Management
Migrating to new cryptographic algorithms and PKI systems requires configuration and issuance of large numbers of new certificates and revoking old certificates for every application, device, and server in an organization. Plus, IT teams must continue to manage all the certificates on an ongoing basis to ensure systems do not fail due to expired certificates. Using manual processes to discover, install, monitor, and renew all the PKI certificates in an organization is labor-intensive and technically demanding.
An automated approach to certificate management also ensures organizations can maintain cryptographic agility to adjust to evolving quantum-safe cryptographic techniques. Automation tools available today, like Sectigo Certificate Manager, allow organizations to quickly update cryptographic algorithms and to revoke and replace at-risk certificates with quantum-safe certificates, and to automate certificate discovery and future certificate renewals.
Other Resources
While the cybersecurity community works to standardize quantum-safe algorithms, free resources can help enterprises understand how this will impact their critical business systems and how to maintain security as new threats loom. Sectigo Quantum Labs has produced the Sectigo Quantum-Safe Certificate Toolkit, a proof of concept solution that allows enterprises and security professionals to evaluate possible solutions. This toolkit provides the ability to generate a private quantum-safe root and intermediate certificate, issue private leaf certificates, and utilize these certificates to create quantum-safe TLS sessions.
Watch the following video demonstration of how to create quantum-safe certificates using the toolkit: