Guide to Passwordless Authentication
Today's IT security teams need to be able to recognize and authenticate identities throughout the enterprise — whether those identities belong to humans, devices, data, or applications. Passwords are a traditional and widely used method of ensuring security, but they are not as effective today as they once were. As IT has evolved, malicious actors have become more sophisticated in their attack methods, and have targeted passwords as a weak link in most IT systems.
These actors have become increasingly adept at:
- Tricking users into entering passwords at phishing websites
- Stealing user's identities in transit across the internet
- Lifting passwords from password repositories
- Discovering places where stolen passwords have been reused
- Obtaining passwords through brute force
According to the 2022 Verizon Breach Investigations Report, compromised credentials are responsible for over 66% of all data breaches in North America, but despite these weaknesses, passwords are still in widespread use. But thanks to passwordless authentication using public key infrastructure (PKI) technology, the long-standing goal of eliminating passwords in the enterprise is finally becoming a reality. By 2022, Gartner predicts 60 percent of large and global enterprises, and 90 percent of mid-size enterprises, will implement passwordless methods to authenticate more than 50 percent of use cases. * https://www.gartner.com/smarterwithgartner/embrace-a-passwordless-approach-to-improve-security/
What Is Passwordless Authentication?
The need for access credentials is pervasive throughout the enterprise. Probably the most top-of-mind authentication use case involves employees using passwords to access their computer or log in to websites and applications. But this is just the tip of the iceberg. Secure authentication is also required for network devices and access points such as WiFi, VPN, and gateways; systems including servers, cloud environments, and databases; and a wide range of other devices such as mobile devices, Internet of Things devices, and network appliances. Some of these applications are behind the scenes and invisible to average users, but are nonetheless a critical aspect of enterprise IT infrastructure.
Passwordless authentication is an authentication method that removes the need to enter in - or remember - passwords or any other knowledge-based secrets. It relies on a cryptographic key pair: a private key and a public key. The public key is provided during registration to the authenticating service, be it a remote server, application, or website, and the private key is stored on the user's device and can only be accessed with the use of biometric authentication (such as with voice, fingerprint, or facial recognition), hardware tokens, or other passwordless factors. In most common implementations users are asked to enter their public identifier (username, mobile phone number, email address, or any other registered id) and then complete the authentication process by providing a secure proof of identity in the form of an accepted authentication factor.
A popular example of passwordless authentication is biometric logins on smartphones. Many newer smartphones now include fingerprint and facial recognition options to bypass lock screens, as well as fingerprint recognition to access many of the installed apps.
Categories of Acceptable Authentication Factors
These factors classically fall into two categories:
- Ownership factors ("Something the user has") such as a mobile phone, one-time password (OTP) token, smart card, or hardware token (such as those email magic links you get when you forget your password).
- Inherence factors ("Something the user is") like fingerprints, face or voice recognition, retinal scans, or other biometric identifiers.
Some designs might also accept a combination of other factors such as geo-location, network address, or behavioral patterns and gestures.
Passwordless Authentication vs MFA & 2FA
Passwordless authentication should not be confused with multi-factor authentication (MFA) or two-factor authentication (2FA). MFA and 2FA look to enhance authentication security beyond the use of a simple password by introducing additional authentication factors such as SMS push notifications, OTPs, or hardware tokens. Today's MFA passwordless authentication relies on the FIDO2 standard (FIDO stands for Fast IDentity Online and FIDO2 is just an umbrella term for the combination of WebAuthn and Client to Authenticator Protocol (CTAP)).
In contrast, passwordless authentication uses just one highly secure factor to authenticate identity, making it faster and simpler for users than most MFA methods. It is also possible to implement passwordless multi-factor authentication (MFA), as long as passwords are replaced with other authentication factors.
Passwordless Authentication Security
Passwordless authentication is safer and more secure. The human element associated with using, remembering, and managing passwords leads to security risk. People often find it difficult to remember passwords, and fall back on a variety of tactics to manage password complexity in their lives. These include the use of easily predicted passwords, reuse of passwords across multiple systems, and sharing or storing passwords in an unsecured manner. Password reuse and the use of predictable passwords can lead to vulnerabilities to a wide range of attacks, make cybercriminals' lives easier, and leave you open to account takeover and other security threats.
Guards Against Attacks
Eliminating passwords by implementing passwordless authentication eliminates the following attack vectors:
- Phishing
- Social engineered spear phishing
- Keyloggers
- Credential stuffing
- Credential replay
- SIM swapping
Offers Security Advantages and Enhanced Usability
Passwordless authentication methods remove risk associated with having single points of failure and thus are more safe and secure than simple password authentication. It also offers advantages over MFA, as implementations using OTPs or push notifications to mobile devices can create challenges for the end user if the device is lost, stolen or sometimes even when it is upgraded.
It also provides a better user experience than either simple password authentication or MFA: not only are users not required to remember complicated passwords and comply with different security policies, they are also not required to periodically renew their passwords. And they don't have to deal with the hassle of hardware tokens, MFA, or secondary authentication on a mobile device.
This increased usability is not just a nice-to-have; it is actually a crucial factor in providing improved enterprise security as the most effective security solutions are those that people will actually use. By removing the reliance on usernames and passwords, and all the problems they entail, passwordless authentication improves the user experience while enhancing your organization's security and reducing your overall attack surface.
PKI Offers the Best Passwordless Authentication Solution
Whatever method organizations choose to authenticate digital identities, they need to be:
- Strong enough not to be stolen
- Future-proof so that the enterprise can stay ahead of evolving threats.
The best method of replacing passwords is Public Key Infrastructure (PKI), the gold standard for authentication and encryption and a cornerstone of enterprise cybersecurity. There is no stronger, easier-to-use authentication and encryption solution than the digital identity provided by PKI.
PKI has been in use for decades and has become an integral part of modern life. Websites, networked devices, mobile devices, and Internet of Things devices all routinely use PKI to authenticate, digitally sign, and encrypt data to protect it from theft or tampering, often without our notice.
Public & Private Key Pair Technology
PKI certificates rely upon public key/private key pair technology, that when used together act as the basis for providing secure access credentials. The private key is secret, known only to the user, and should be encrypted and stored safely on the user's device. In contrast, the public key is shared freely with any user, device, or server to which the user wishes to connect. These keys are normally managed by an organization's IT team, or better yet, with the help of a trusted Certificate Authority (CA) to ensure they are stored safely.
Why Password-Based Authentication Is Not Recommended and Why PKI is Best
To protect a password-protected identity from being stolen, the password must be kept secret. But in order to use it, the password must be shared. This is the primary reason that passwords fail: they rely on sharing a secret that may be accidentally, or purposefully, misused.
By contrast, with PKI there are no secrets to be shared or intercepted. Authentication happens when the user proves she or he is in possession of the private key. Then, the transaction signed by the private key is verified by the public key. This is superior to password-based authentication for a number of reasons:
- The private key never leaves the client. This is in contrast to passwords, which are easy to share intentionally—or unintentionally via phishing attacks.
- The private key cannot be stolen in transit, because it is never transmitted. Unlike passwords, which can be stolen in transit through the internet, the private key is never transmitted.
- The private key cannot be stolen from the server repository. Passwords stored in central server repositories can be stolen; private keys are known only to the user's device and are not stored centrally.
- There is no need for users to remember passwords or enter usernames. The user's device simply presents her or his private key stored on his device, providing a more seamless experience.
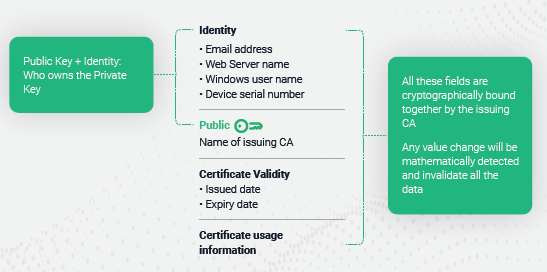
Figure: PKI-based identity certificates offer the easiest, most secure form of passwordless authentication.
It is possible to implement passwordless authentication using other factors and not PKI. However, PKI is simpler, more secure, and more scalable than other methods of passwordless authentication.
For example, most methods of MFA are not actually passwordless and still require a password, supplemented by a code from an authenticator app, entry of hardware tokens, OTP, or push notification to a mobile device. These methods of MFA are still prone to password interception, and thus do not solve the risks associated with passwords. Further, by requiring additional authentication steps they provide a more frustrating user experience. https://sectigo.com/resource-library/pki-vs-mfa-infographic
What Technology Is Used to Generate Private and Public Keys?
To create the digital identity, the public and private key are both generated, and the pair is associated with each other using a strong public key cryptography algorithm. Key generation can be performed using an automated certificate management system, like Sectigo Certificate Manager, or it can be performed manually by a system administrator. Generating and storing keys manually can be accomplished on the most common operating systems.
The most common mathematical algorithms used to generate keys are Rivest–Shamir–Adleman (RSA) and Elliptic Curve Cryptography (ECC). RSA and ECC algorithms use various computation methods to generate random numeric combinations of varying length so that they cannot be exploited with a brute force attack. The key size or bit length of keys helps determine the strength of protection. 2048-bit RSA keys or 521-bit ECC keys offer sufficient cryptographic strength to keep hackers from cracking the algorithm.
Administrative Benefits
Passwords are costly for IT teams to administer and support. Password resets and password management both create a significant amount of work for IT help desks. Further, they reduce employee productivity by disrupting their ability to work while they wait for their passwords to be reset.
Forrester Research estimates that large organizations spend up to $1 million per year on staffing and infrastructure to reset passwords. In contrast, passwordless authentication reduces IT administration burden, providing a number of benefits, including:
- Reduced total cost of ownership – IT teams no longer need to be bothered with setting password policies, detecting leaks, resetting forgotten passwords, or complying with password storage policies and regulations.
- Better visibility of credential use – since passwordless authentication credentials are tied to a specific device or inherent user attribute, they can't be massively (and inappropriately) used by multiple individuals. As a result, access management becomes tighter.
- Management at scale – IT teams can manage multiple logins without additional password fatigue or complicated registration.
Steps to Implementing Passwordless Authentication Using PKI
Here’s a general overview of the steps to take towards a passwordless experience:
- Perform an Audit of Employees, Applications, Infrastructures, and Login Flows
- Develop Phases For Your Approach
- Identify Use Cases for PKI Authentication
- Streamline Authentication Workflows
- Apply Analytics and Adaptive Access Policies
- Switch to a Fully Passwordless Experience
Implementing passwordless authentication is no small task, especially when you’re dealing with a large number of employees, a large number of applications, hybrid cloud-based and on-premises infrastructures, and/or complex login flows. Achieving a completely passwordless environment is best pursued using a measured, phased approach. We go into detail about each of these steps below.
The most appropriate path to pursuing passwordless authentication entails:
- Identify use cases for PKI authentication. Most enterprises will want to start with select specific use cases, devices, and/or applications and pursue a measured, stepwise rollout. This will reduce the risk and allow your IT teams to come up the learning curve in a targeted, controlled manner.
- Streamline authentication workflows. A key aspect of streamlining the user experience and eliminating potential authentication points of failure involves reducing the number of places where credentials are required. If you aren't already, look into using single sign-on (SSO) technologies for SAML-based applications in the cloud, and integrate application workflows using access and authentication proxies for on-premises services. Alternatively, implement MFA using a biometric authenticator, powered by PKI, as the second factor to provide additional authentication security. This will enable you to phase in the use of PKI as you roll out your biometric technology throughout your workforce.
- Build trust in PKI-based authentication. Apply analytics and adaptive access policies based on the context of users, devices, locations, and behavior to confirm that your authentications can be trusted. Confirm that you are not seeing anomalous user behavior or risky devices to confirm that users are who they say they are and are using appropriate devices to access your network.
- Switch to a fully passwordless experience. Eliminate the password component of authentication altogether, relying exclusively on the PKI-based identity certificates, to allow users and devices to access your network and applications without the additional steps required by MFA and biometric solutions.
How to Automate PKI Management for Passwordless Authentication
Proper PKI certificate management is essential for organizations to provide a scalable, cost-effective, and secure method of authenticating access to mission-critical business systems and data. But managing digital certificates manually (individually) can be time-consuming and prone to error, which in itself can introduce security risk.
Key management is further complicated by the fact that many organizations have thousands, if not millions of certificates stored throughout their environment. The security that certificates provide can be easily undermined if IT are unable to manage certificate expirations, revocations, and renewals on an ongoing basis. Systems operating using expired certificates represent a security risk. Using manual processes to discover, install, monitor, and renew all the PKI certificates in an organization is risky, labor-intensive, and technically demanding.
By taking an automated approach to certificate management, you reduce risks of certificate expiration while decreasing the burden on your team of administering certificates at scale. Partnering with a service provider that offers enterprise-grade automation tools, like Sectigo Certificate Manager, can allow you to automate issuance and lifecycle management of all of the certificates throughout your entire organization, across a wide variety of passwordless authentication use cases.
To learn more about passwordless authentication and how to implement it in the enterprise read the white paper The Passwordless Enterprise: Using PKI to Replace Passwords for Identity and Access.
