-
Listen Now

EPISODE 14
Broadcast Date:
May 2, 201922 minutes
 Podcast May 02, 2019
Podcast May 02, 2019Root Causes 14: P2P Vulnerability in IoT Devices
Recent research reveals millions of consumer IoT devices lack authentication or encryption. Join our hosts as we discuss the nature of IoT-based botnets.
-
Blog Post Apr 26, 2019
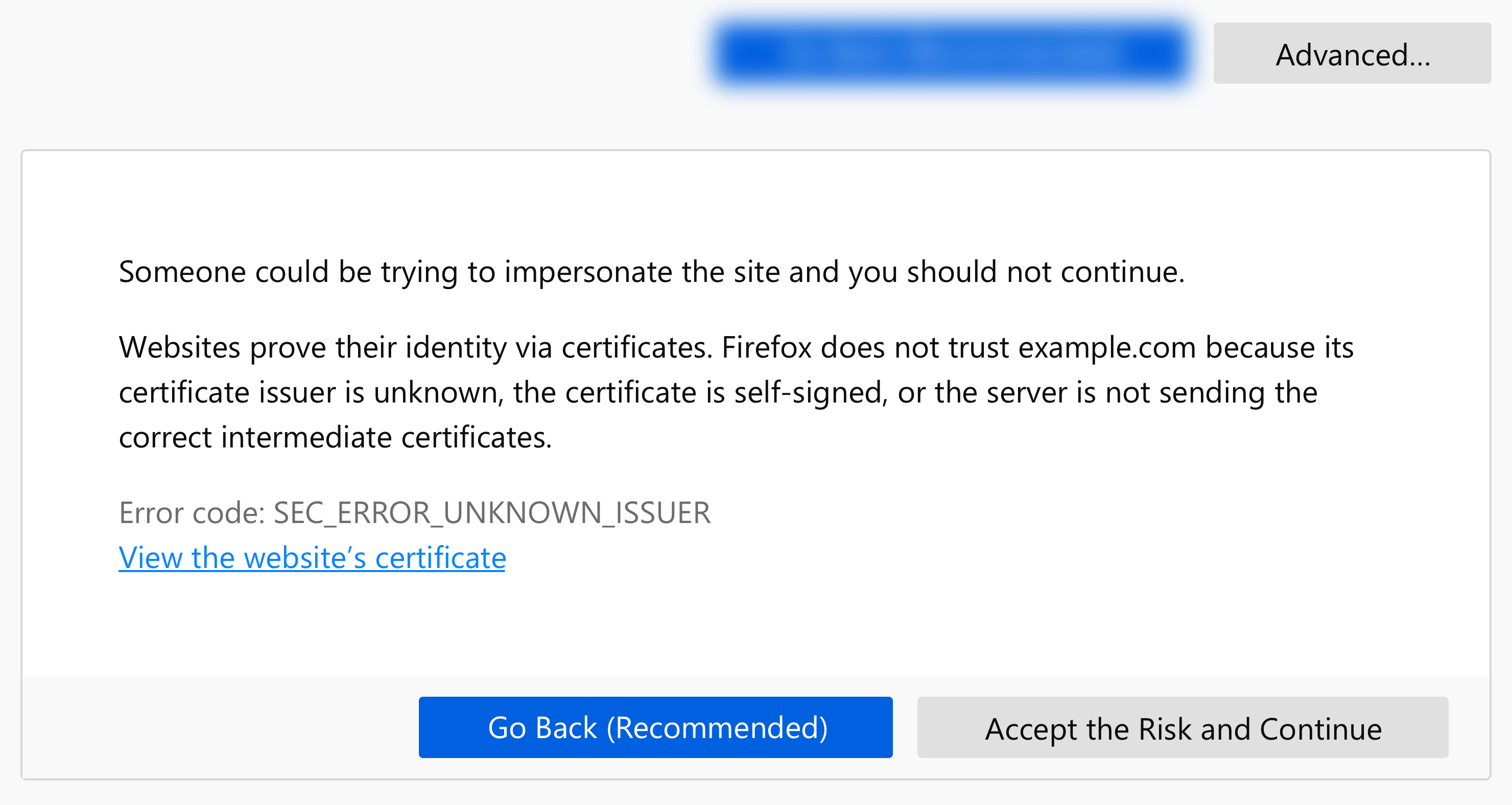
What the Latest Firefox Update Means for SSL Certificates
Learn what impacts the latest Firefox 66 update will have on your SSL certificates & what it means for your website security & user confidence.
-
Listen Now

EPISODE 13
Broadcast Date:
April 25, 201920 minutes
 Podcast Apr 25, 2019
Podcast Apr 25, 2019Root Causes 13: PKI for IoT
The proliferation of Internet of Things (IoT) devices has begun to outpace security. Learn more about the role of identity in protecting IoT devices.
-
Listen Now

EPISODE 12
Broadcast Date:
April 16, 201919 minutes
 Podcast Apr 16, 2019
Podcast Apr 16, 2019Root Causes 12: PKI in the News
It was a busy news week for PKI and authenticated identity, and our hosts run through four current stories to clarify them. Tune in to learn the latest.
-
Blog Post Apr 11, 2019
Should the EV-SSL-Enabled Interface Be Called a “Green Address Bar?”
When Extended Validation (EV) SSL first launched in 2007 people began to refer to the "green address bar." Browser interfaces have evolved since then. Perhaps the way we refer to how these TLS / SSL certificates display should evolve as well.
-
Listen Now

EPISODE 11
Broadcast Date:
April 9, 201914 minutes
 Podcast Apr 09, 2019
Podcast Apr 09, 2019Root Causes 11: Authentication Is Not for the Authenticated
With much debate about the importance of authentication in digital systems, it is key to remember the purpose of identity in cyber interactions.
-
Listen Now

EPISODE 10
Broadcast Date:
April 3, 201919 minutes
 Podcast Apr 03, 2019
Podcast Apr 03, 2019Root Causes 10: S/MIME Automated Deployment
S/MIME certificates indicate the authentic identity of the sender and enable encryption. Find out what the challenges to past adoption have been.
-
Blog Post Mar 26, 2019
Why CAs Charge More for Extended Validation SSL
Extended Validation (EV) SSL certificates are one of three standard SSL certificate types issued by Certificate Authorities: DV, OV, and EV. What makes EV certificates different from the others is that they provide the highest assurance that the domain is NOT associated with a bad actor. When users see a company-branded address bar next to the URL, they can know that they are on a trusted domain.
So is an EV SSL certificate right for you? In order to determine this, it’s important to understand why the cost is higher than other certificate options, the unique value it provides, and how the issuance process works.
-
Listen Now

EPISODE 09
Broadcast Date:
March 25, 201915 minutes
 Podcast Mar 25, 2019
Podcast Mar 25, 2019Root Causes 09: 63-bit Serial Numbers
A recently discovered flaw in common practices reveals that potentially millions of active SSL certificates fall short of cryptographic requirements.
-
Listen Now

EPISODE 08
Broadcast Date:
March 18, 201919 minutes
 Podcast Mar 18, 2019
Podcast Mar 18, 2019Root Causes 08: Free PKI Is Not Free
A "free" Microsoft CA was alluring to enterprises in the 2000s. Learn about the seven common use cases where your traditional CA no longer does the job.
-
Blog Post Mar 13, 2019
63-Bit Password Emphasizes Role of Automation in Enterprise PKI
Industry PKI experts recently have discovered a flaw in certificate generation practices that employ the commonly used EJBCA CA tool, which can result in serial numbers with 63 bits of entropy as opposed to the 64 bits required by public certificate guidelines. Episodes like this one put a spotlight on the value of automation in certificate practices. Automated capabilities enable the consistently correct maintenance, revocation, and replacement of a large number of certificates with little human interaction required.
-
Blog Post Mar 12, 2019
New Research Regarding Online Criminal Marketplaces for Certificates
A recent study by Georgia State University suggests that criminal online marketplaces feature a steady supply of TLS / SSL certificates from all major public CAs. Sectigo is eager to work with researchers like these and others to help reveal criminal activity and create strategies to mitigate its effectiveness without preventing legitimate business from benefiting from public certificates.