The risks of expired SSL certificates for enterprise organizations
Expired SSL certificates can expose enterprises to security risks, downtime, loss of customer trust, and financial and reputational damage. Proper certificate renewal processes are essential to avoid these issues, especially for large organizations with many certificates to manage.
Table of Contents
Secure Socket Layer (SSL) / Transport Layer Security (TLS) certificates form the basis of modern website security and authentication. These certificates are widely used by organizations of all types and across all sectors.
Meant to establish encrypted connections between websites and web browsers, SSL/TLS certificates ensure data integrity while authenticating the identity of a website and safeguarding data transmission.
Unfortunately, many organizations struggle to keep their SSL certificates up to date, especially those dealing with hundreds or even thousands of digital certificates. Manual renewal processes are time-consuming and prone to errors, and, as overburdened IT departments take on a growing array of security tasks, certificate lifecycle management processes often suffer.
This is a common problem among smaller enterprises — but large corporations are also vulnerable. During the last several years, certificate outages have hit headlines, prompting considerable downtime, loss of customer trust, and with it, major financial losses. Add reputational damage, and it's easy to see why avoiding expired SSL certificates with strong certificate renewal processes is such a priority.
Companies that have faced major certificate outages
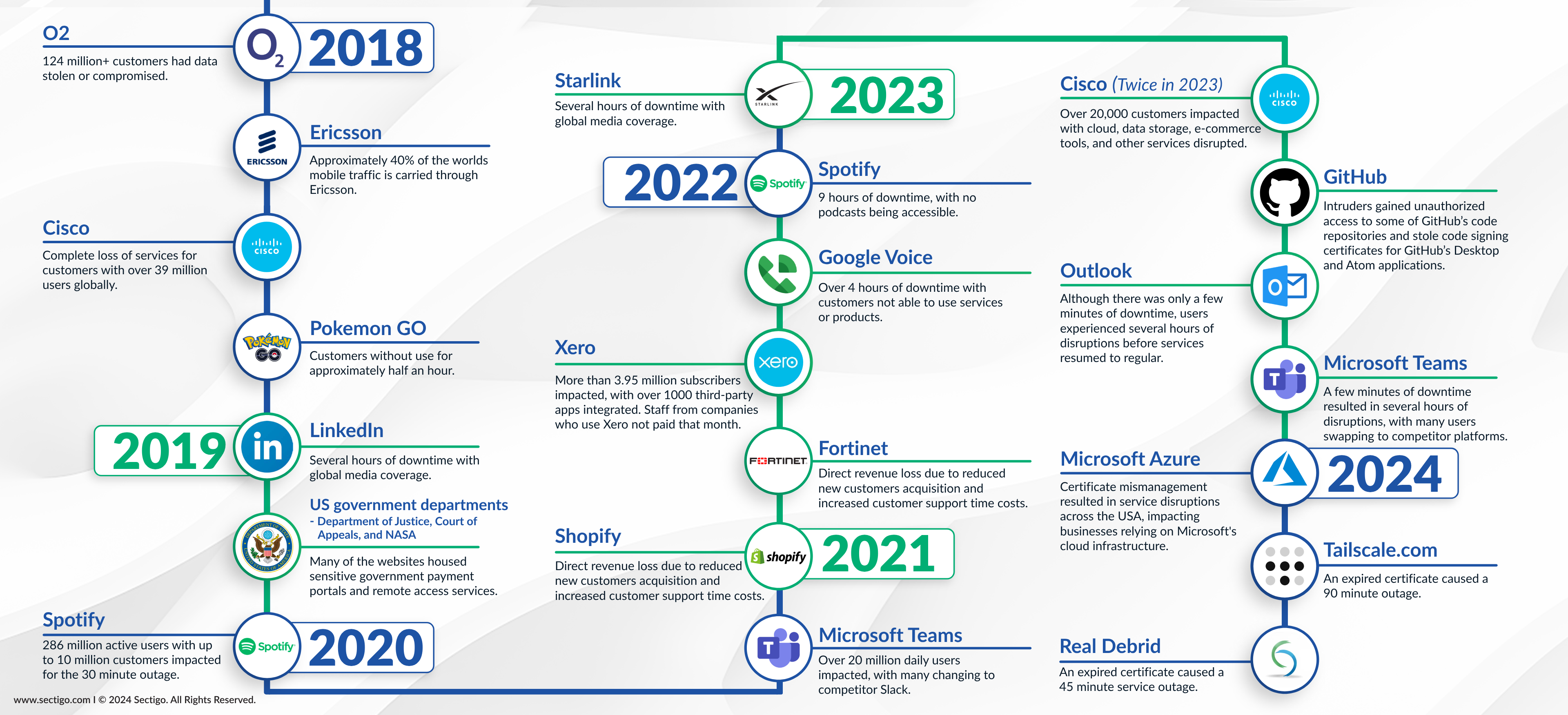
Timeline of certificates outages in big companies
Certificate outages occur far too often, prompted by the rapid expansion of SSL/TLS certificates in an increasingly complex and vulnerable digital space. Many seemingly well-protected and well-run organizations have fallen victim to these issues, and unfortunately, since SSL certificate validity periods will soon shrink to just 90 days, many more will become prone to outages. This could prompt significant reputational damage while also leaving organizations vulnerable to cyberattacks from increasingly sophisticated hackers.
Certificate expirations are common, but not inevitable. With the right approach to certificate lifecycle management (CLM), it is possible to dramatically reduce the risk of outages while bringing a more structured and reliable approach to certificate renewal. Still, it is important to remain fully aware of key vulnerabilities. To reveal the extent of SSL expiration issues — and the need for vigilance — we have highlighted several familiar organizations that have dealt with alarming outages.
Ericsson (2018)
Carrying approximately 40 percent of the world's mobile traffic, Ericsson has long been a trusted name in telecommunications. Although Ericsson typically provides reliable coverage, a major lapse occurred in 2018, when an expired certificate caused problems for millions of European customers and even many in Japan.
IT journalist Davey Winder told Forbes, "I would have expected a company as large as Ericsson to know better and have the relevant failsafe processes in place to prevent such an event." He added, however, that those in the cybersecurity space were all too familiar with disruptive certificate expiry.
Ericsson CEO Börje Ekholm later claimed that the software responsible for this outage was decommissioned. This fiasco clearly revealed the need to keep "a firm handle on the certificates installed in business-critical systems," as highlighted by Sectigo's Tim Callan.
LinkedIn (2019)
LinkedIn is a trusted name in the modern social media sphere, but the platform has suffered a few significant tech oversights through the years. One of the most concerning occurred in 2019, when Microsoft (which had previously acquired LinkedIn) allowed an SSL certificate to expire. While LinkedIn appeared to have renewed the certificate in question as of May, 2019, this update was not properly reflected by the server.
This was by no means the first time LinkedIn suffered downtime due to a certificate renewal oversight; this also occurred in 2017, when millions of website users were unable to log into their accounts. Security researcher Alan Woodward explained, "It's not the first big name to forget to renew certificates, and it is easy to forget subdomains, but really, with the reminders that the CA [certificate authority] sends, it’s surprising it still happens."
Microsoft Teams (2020)
Microsoft Teams facilitates real-time collaboration with instant messaging, video calls, file storage, and many other capabilities. In 2020, however, all this was called into question for previously trusting users, who suddenly faced major disruptions as Microsoft Teams went down for several hours.
As users attempted to sign in, they received error messages, indicating that the app was unable to establish necessary HTTPS connections. An outage notification from Microsoft explained: "An authentication certificate has expired, causing users to have issues using the service." This was especially concerning given the company's use of System Center Operations Manager to help detect certificate expiration.
Google Voice (2021)
In February, 2021, an expired TLS certificate prevented users from fully leveraging the telephone service Google Voice. For a full four hours, these users could not make Voice over Internet (VoIP) calls.
Later, a root cause analysis explained, "Due to an issue with updating certificate configurations, the active certificate in Google Voice frontend systems inadvertently expired...During the impact period, any clients attempting to establish or reestablish an SIP connection were unable to do so."
Google's engineers spent two hours investigating the outage, although Google's Issue Summary did not reveal what, exactly, they examined during this time. An alert eventually notified these professionals of the concerns underscoring the outage, but not before an unacceptable amount of downtime had occurred.
Spotify (2022)
Spotify has made its mark in the podcast space with the platform Megaphone, which helps professional podcasters publish their programs and grow their audience. This platform suffered a major outage in 2022, however, as a result of a missed certificate renewal.
In a statement, spokesperson Erin Styles explained, "Megaphone experienced a platform outage due to an issue related to our SSL certificate. During the outage, clients were unable to access the Megaphone CMS and podcast listeners were unable to download podcast episodes from Megaphone-hosted publishers."
This prevented podcast listeners from listening to their favorite shows for a shocking eight hours — long enough for previous Spotify and Megaphone devotees to lose confidence in their favorite streaming provider. Even after access was technically restored, many users were unable to make full use of the Megaphone content management system.
Cisco (2023)
The company published a bulletin revealing that using vEdge SD-WAN appliances might suffer losses of service if they updated their devices. These issues were also expected to negatively impact port-hopping and topology changing.
This fiasco impacted over 20,000 customers. One user told The Register, "All vEdge based SD-WAN customers are sitting on a time bomb, watching the clock with sweaty palms, waiting for their companies' WAN to implode and/or figuring out how to re-architect their WAN to maintain connectivity."
Unfortunately, this was not the first time that Cisco's customers suffered due to certificate outages. In 2018, an SSL certificate expired within Cisco's VPN kit, also prompting doubts about CIsco’s ability to protect end users.
The critical role of automated certificate lifecycle management
The examples highlighted above are not meant to alarm, but rather, to convey the need for vigilance in managing and renewing SSL/TLS certificates. Yes, digital certificates remain crucial, but they must be underscored by a reliable process to ensure consistent coverage. Although certificate authorities (CAs) offer notifications prior to upcoming expiry dates, it may take a more concerted effort to prevent expired certificates that lead to outages.
Automated certificate lifecycle management promises to bridge the gap, limiting the potential for unexpected expiration (and associated disruptions) by ensuring that digital certificates are renewed prior to their anticipated expiration dates. Meanwhile, a centralized approach to certificate management offers better visibility into certificate status, ensuring maximum oversight for numerous certificates.
Automated strategies also drive crypto agility, which has been identified as a key quality for avoiding outages moving forward. This term references organizations' ability to adapt to evolving algorithms while continuing to promote maximum continuity for cybersecurity infrastructure. Crypto-agile systems are better capable of renewing certificates promptly and avoiding outages.
Don’t become the next victim of an SSL certificate outage
Given the high stakes and security risks that come along with expired SSL certificates, there really is no substitute for automated certificate lifecycle management. Unleash the power of automated issuance and management with Sectigo Certificate Manager (SCM) — a purpose-driven platform designed to bring greater confidence and reliability to the entire digital certificate lifecycle. Learn more today, schedule a demo, or take the next step with a free trial.
Want to learn more? Get in touch to book a demo of Sectigo Certificate Manager!
Related posts:
Why SSL certificates expire: exploring the benefits of shorter validity periods
The impact of 90-day SSL certificates on enterprise security
How businesses should prepare for shorter SSL/TLS certificate validity periods
