How to Keep Hackers Away from Tomorrow’s Smart Cities

Everything in our cities is connected; traffic controls, vehicles, and buildings—to the point that cities are smart enough to adapt to human needs and are engineered to function at the highest possible levels of power efficiency and effectiveness. But with this connectivity come dangerous vulnerabilities.
While it is estimated that more than 2.3 billion connected devices are already deployed in smart cities worldwide, we are still in the early stages of the smart city revolution. Everything is connected; traffic controls, vehicles, and buildings—to the point that cities are smart enough to adapt to human needs and engineered to function at the highest possible levels of effectivity, power efficiency, and safety.
The common threads to all of this are infrastructure, communications, and intelligence. All three of these essential components are vulnerable to hacking and cyberattacks. In recent years, Atlanta, Baltimore, Greenville, NC and other cities have experienced high-profile attacks. Such incidents will only become more frequent unless manufacturers of internet-connected devices and internet infrastructure used across municipalities adopt more suitable security policies, procedures, and protocols.
In 2018, Atlanta was hit by the Samas or SAMSAM ransomware, which crippled the city for about two weeks and impacted about 30% of the city’s “mission critical” software applications. Hackers demanded a ransom of $50,000 in bitcoin but the city declined to pay it. Atlanta officials reported that a ‘decade’s worth of legal documents and ‘years’ of police dashboard camera evidence have been wiped from their computers with far-reaching consequences for law and order. The Atlanta Journal Constitution reported that the hack cost the city around $17 million.
A year later, Baltimore was hit by the RobbinHood ransomware in an attack costing the city more than $18 million. The attack locked down servers and left the city government without email or telecommunications, disrupted disrupting real-estate transactions and bill payments – as well as emergency services.
Why are cities so vulnerable to dangerous attacks?
Let’s start with the infrastructure. Cyber criminals have been able to reprogram traffic lights and controls, causing major traffic jams. Others have been able to access the controls of various digital traffic signs and cause a great deal of mischief.
Most of those hacks were not life-threatening. However, that will change with the arrival of autonomous vehicles. Soon, delivery trucks, buses, taxis, and personal vehicles will be autonomous. One of the promises of AVs is that, by talking to each other and to a city’s traffic system, these autonomous vehicles will operate much more efficiently and safely. However, this communication requires close coordination between vehicles—possibly traveling at high speeds, just inches apart.
What happens if one of these vehicles gets hacked and loses its communication and cannot coordinate with other vehicles? At a minimum, it can cause traffic to get tangled. At worst, the hack could cause serious accidents, possibly resulting in injury and loss of life for the passengers and/or nearby pedestrians.
Another risk for smart cities is the environment controls within buildings. Ensuring optimum temperature and humidity levels within retail stores, offices, and residences is a complex dance, balancing energy use versus occupant comfort. Once again, a hacker who gains access to the environmental control can wreak havoc, making the buildings uninhabitable or potentially even unsafe. With access to a building’s controls, the hacker could control the operation of elevators, escalators, and internal doors. A malevolent hacker could set off fire alarms and trigger fire extinguishers and sprinkler systems, causing a great deal of needless disruption as emergency personnel rush to react to incidents that may or may not actually be occurring.
And of course, let us not forget physical security. A hacker who gains access to a building’s management system could remotely open and close external doors, enabling criminals to enter, as well as trapping workers and residents inside a building.
Or consider the ways utilities could be remotely controlled. Hackers who gain access to critical systems could turn on and off the power to a city, turn off heat on a freezing day, cut water supplies, or meddle with sanitation and sewer systems. All of these utilities are controlled over the internet and could be a target for a hacker.
All this is in addition to the vast set of traditional IT systems required to keep every city running. Government, schools, first responders, and the vendors and service industries that keep them running, all depend on digital operations to stay on track. Imagine the impact to a city and its citizenry if the computerized back-office stops working for important services like food and fuel distribution. A cyberattack against a city’s private industries can be as disruptive to municipal operations as a direct attack on the smart infrastructure itself.
An attack doesn’t need to directly control systems to wreak havoc. As with the ransomware attacks above, criminals can easily hold hostage critical city systems and infrastructure networks, demanding hundreds of thousands of dollars, if not millions, to release a city from their stranglehold.
One thing about a malware infection is that it can spread. A hacked traffic light in an intertwined maze of internet-connected “things” could spread to the traffic communication system. From there, it could spread to the city’s emergency and first responder system. And from there…it could potentially cripple entire systems across a smart city.
So how do we protect the smart city?
The first step is securing the networked and enterprise level infrastructure systems—ensuring that only approved people and commands can access these machines. By using the latest network security appliances and certificate-based authentication for all systems, attacks on network infrastructure can be limited.
Second, we must secure the various connected devices that people use on a daily basis, from smartphones and smart watches, notebooks, tablets and laptops, to IoT devices like health and exercise monitoring devices, building control systems, traffic management systems, etc. Each must have security built into the device to avoid becoming a target for hackers. Security solutions are available for laptops, smartphones and tablets, but IoT devices require specialized embedded security solutions. These smaller devices do not have the resources to run traditional security solutions. They require the specialized security solutions designed for IoT devices, including secure boot, secure firmware updates, secure communication protocols, and strong authentication systems based on digital certificates.
How about the cars and autonomous vehicles? Today’s cars are essentially networks on wheels. Unfortunately, most of the networks, sensors, and electronic control units (ECUs) in these vehicles are not adequately protected. And as vehicles become even more sophisticated, adopting higher levels of autonomy, they will become even more vulnerable to attack.
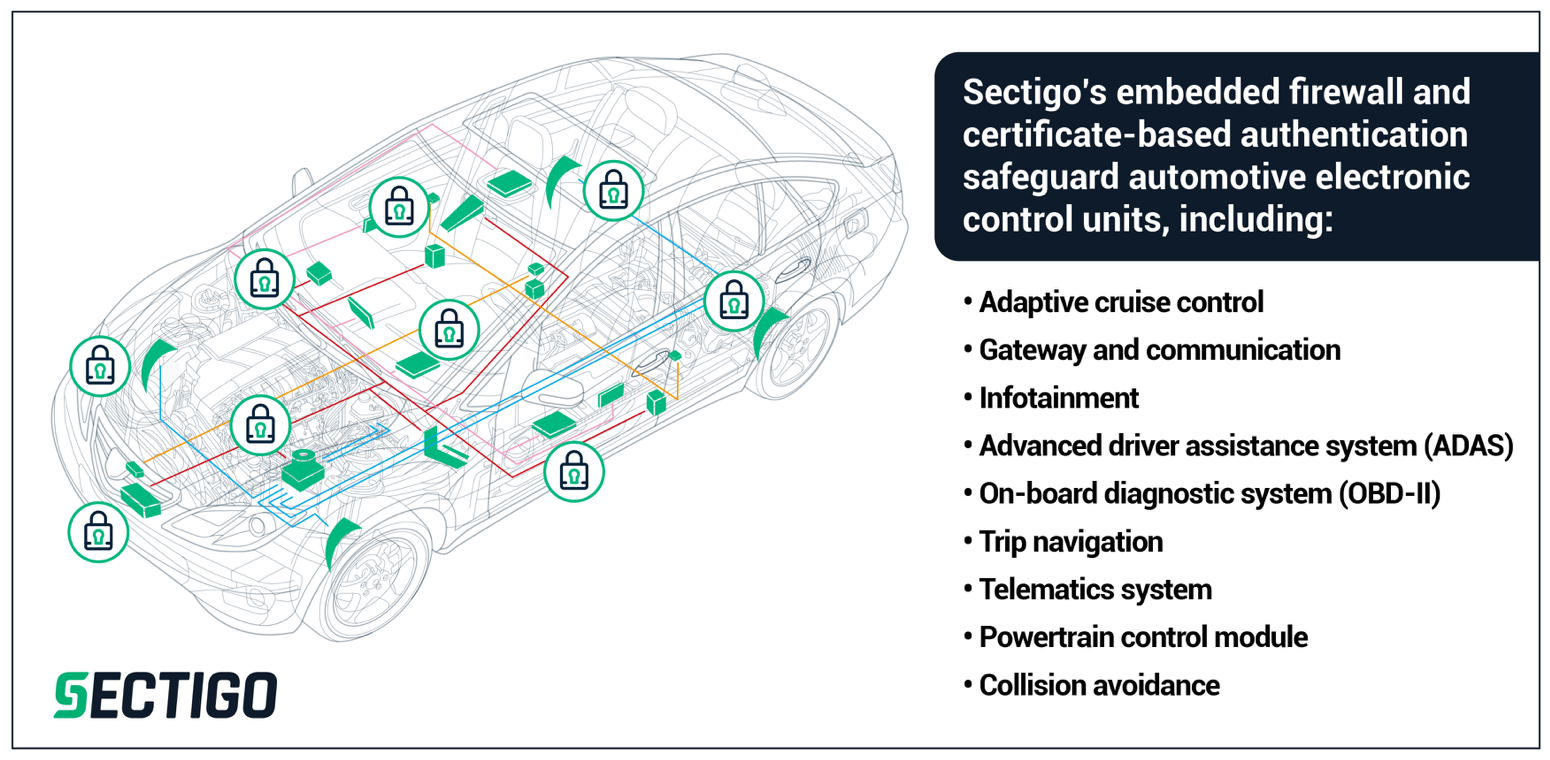
It is possible to protect the car’s brains (the ECUs), as well as its sensor and communication networks, by implementing embedded security solutions to protect the car’s data, control systems, and communication.
Finally, we must continue to pay attention to the traditional IT systems that keep municipal data, employees, web sites, and services operational. Would-be attackers already possess a full kit of tools and techniques for attempting the breach against this kind of infrastructure. IT departments must ensure they employ the best and most current security practices and solutions to prevent the damage that can come from compromising their traditional architecture.
As our world becomes more sophisticated and our cities, our utilities, our buildings, and our cars, become home to increasingly complex computer and data networks, their vulnerability to bad actors and cyberattacks continues to grow.
There are proven steps that city and network managers can take now to mitigate these risks. There are protocols and technologies that connected device developers and manufacturers can implement now, as well as in the future, to inoculate against cyberattacks. It is up to our technology leaders, our cutting-edge engineers and designers, and our STEM training universities, to learn, master and utilize the latest generation of security best policies and technologies—making security a priority, from the assembly line to the deployment and management of systems.
