Digital signatures: What they are & how they work


A digital signature is a PKI-based digital certificate that authenticates the identity of the signer and ensures electronically transmitted documents and digital messages have not been forged or tampered with. Digital signatures are similar to physical signatures in the sense that both are unique to the signer, except that in the case of digitally signed documents, a digital signature offers far more security and the assurance of the document’s origin, identity, and integrity. Based on the highest standard of security, digital signatures are legally binding in the United States and many other countries.

Digital signature vs electronic signature
Electronic signatures, commonly referred to as e-signatures, are a broad set of solutions that use an electronic process for accepting a document or transaction with a signature. As documents and communication are increasingly paperless, businesses and consumers worldwide have embraced the speed and convenience of these types of signatures. But there are many different types of electronic signatures, each allowing users to sign documents digitally and offering some degree of identity authentication.
Digital signatures are one of those electronic signature technologies and are the most secure type available. Digital signatures use PKI certificates from a Certificate Authority (CA), a type of Trust Service Provider, to ensure identity authentication and document integrity by encrypted binding of the signature to the document. Other, less secure e-signature types may use common electronic authentication methods to verify the signer’s identity, such as an email address, a corporate username/ID, or a phone number/PIN.
As a result of different technical and security requirements, electronic signatures vary in industry, geographic, and legal acceptance. Digital signatures comply with the most demanding regulatory requirements, including the United States Federal ESIGN Act and other applicable international laws.
How do digital signatures work?
Digital signatures use public key infrastructure (PKI), which is considered the gold standard for digital identity authentication and encryption. PKI relies upon the use of two related keys, a public key and a private key, that together create a key pair to encrypt and decrypt a message using strong public key cryptography algorithms. Using both public and private keys that are generated using a mathematical algorithm to provide the signer with their own digital identity, a digital signature is generated and encrypted using that signer’s private key, and also a timestamp of when the document was signed using the key. These keys are normally stored safely thanks to the help of a trusted CA.
Both public and private keys are generated using a mathematical algorithm; they provide the signer with their own digital identity and then a digital signature is generated and encrypted using that signer’s corresponding private key. A timestamp of when the document was signed using the key is also generated. These keys are normally stored safely thanks to the help of a trusted CA.
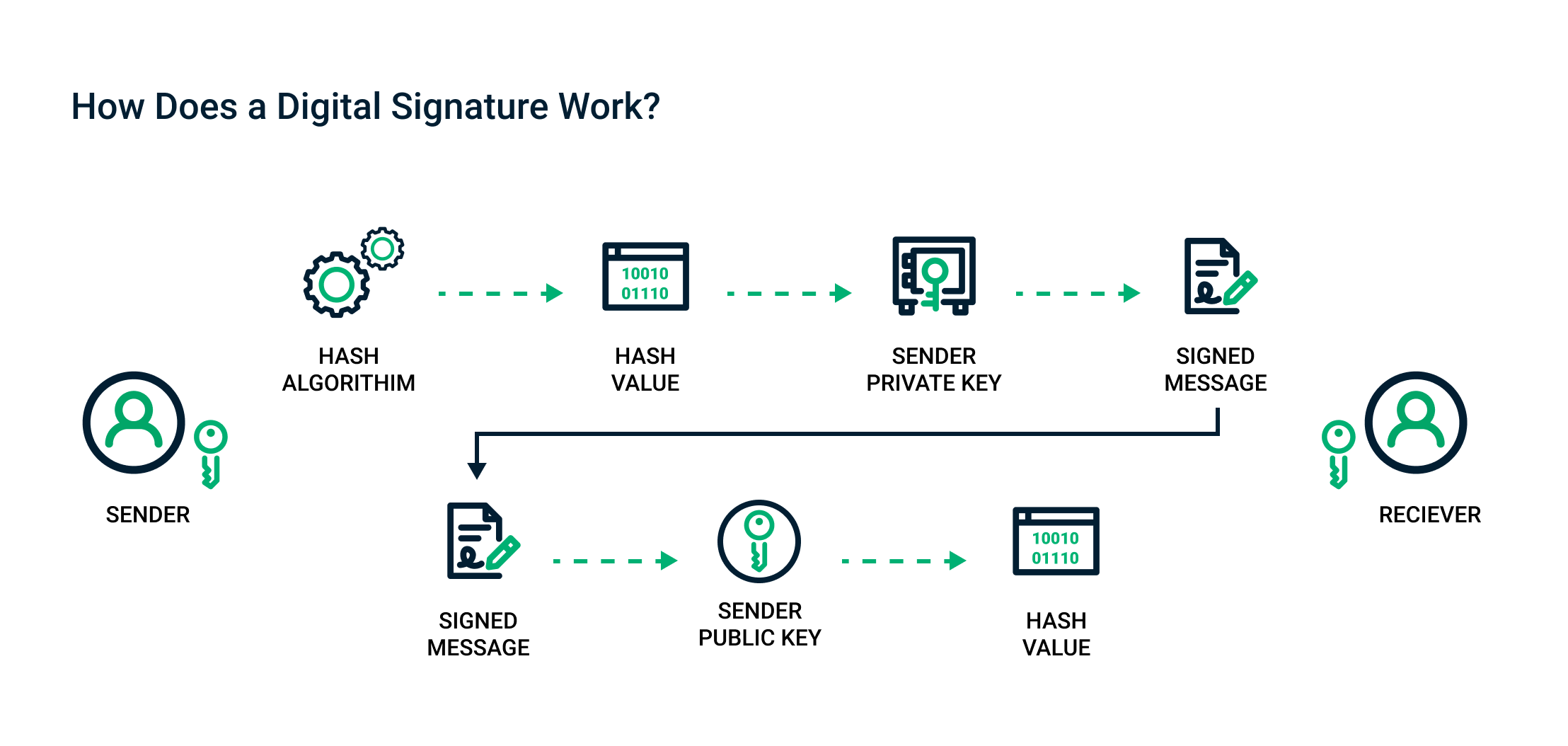
Here is how sending a digital signature works:
- The sender selects the file to be digitally signed in the document platform or application.
- The sender’s computer calculates the unique hash value of the file content.
- This hash value is encrypted with the sender’s private key to create the digital signature.
- The original file along with its digital signature is sent to the receiver.
- The receiver uses the associated document application, which identifies that the file has been digitally signed.
- The receiver’s computer then decrypts the digital signature using the sender’s public key.
The receiver’s computer then calculates the hash of the original file and compares the hash it has computed with the now decrypted hash of the sender’s file.
The process to create a digital signature is easy and straightforward for the average user and for enterprises to adopt. You first need a digital signing certificate, which can be acquired through a trusted Certificate Authority like Sectigo. After downloading and installing the certificate, you simply use the digital signing function of the appropriate document platform or application. For example, most email applications provide a “Digitally Sign” button to digitally sign your emails.
When sending out a document signed using a private key, the receiving party obtains the signer’s public key which will allow one to decrypt the document. Once the document is decrypted, the receiving party can view the unaltered document as the user intended.
If the receiving party cannot decrypt the document using the public key, then it signifies that the document has been altered, or even that the signature doesn’t even belong to the original signer.
Digital signature technology requires all involved parties to trust that the individual creating the signature has been able to keep their own private key secret. If someone else has access to the signer's private key, that party could create fraudulent digital signatures in the name of the private key holder.
What happens if either the sender or receiver change the file after it has been digitally signed? As the hash value for the file is unique, any change to the file creates a different hash value. As a result, when the receiver’s computer compares the hash to validate the integrity of the data, the difference in the hash values would reveal the file had been altered. Thus, the digital signature would be shown as invalid.
What does a digital signature look like?
Since the heart of a digital signature is the PKI certificate, which is software code, the digital signature itself is not inherently visible. However, document platforms may provide easily recognizable proof that a document has been digitally signed. This representation and the certificate details shown varies by document type and processing platform. For example, an Adobe PDF that has been digitally signed displays a seal icon and blue ribbon and across the top of the document that shows the document signer’s name and the certificate issuer.

Additionally, it can appear on a document in the same way as signatures are applied on a physical document and can include an image of your physical signature, date, location, and official seal.

Digital signatures can also be invisible, though the digital certificate remains valid. Invisible signatures are useful when the type of document typically does not display the image of a physical signature, like a photograph. The document’s properties may disclose the information about the digital certificate, the issuing CA, and an indication of the document’s authenticity and integrity.
If a digital signature is invalid for any reason, documents display a warning that it is not to be trusted.

Why are they important?
As more business is conducted online, agreements and transactions that were once signed on paper and delivered physically are now being replaced with fully digital documents and workflows. However, whenever valuable or sensitive data is shared, malicious actors who want to steal or manipulate that information for their own gain are ever-present. Businesses must be able to verify and authenticate that these critical business documents, data, and communications are trusted and delivered securely to reduce the risk of document tampering by malicious parties.
In addition to protecting valuable online information, digital signatures do not disrupt the efficiency of online document workflows; in fact they typically help improve document management compared to paper processes. Once digital signatures have been implemented, the act of signing a document is easy and can be done on any computing or mobile device.
In addition, the signature is portable as it is incorporated in the file itself, wherever it is transmitted and on whatever device. Digitally signed documents are also easy to control and keep track of by providing the status of all documents, identifying whether or not they’ve been signed, and viewing an audit trail.
And of course, it is vital these digitally signed agreements are recognized from a legal standpoint. Digital signatures are compliant with important standards like the United States Federal ESIGN Act, GLBA, HIPAA/HITECH, PCI DSS, and US-EU Safe Harbor.
Common uses & examples
Today, digital signatures are commonly used for a variety of different online documents in order to improve the efficiency and security of critical business transactions that are now paperless, including:
- Contracts and legal documents: Digital signatures are legally binding. Thus, they are ideal for any legal document requiring an authenticated signature by one or more parties and assurance that the document has not been modified.
- Sales agreements: By digitally signing contracts and sales agreements, both the seller and the buyer identities are authenticated, and both parties have peace of mind that the signatures are legally binding and that the terms and conditions of the agreement have not been altered.
- Financial documents: Financial departments digitally sign invoices so that customers trust the payment request is coming from the proper seller, not a bad actor trying to scam the buyer into sending payment to a fraudulent account.
- Healthcare data: In the healthcare industry, data privacy is paramount for both patient records and research data. Digital signatures ensure that this sensitive information has not been altered when shared between consenting parties.
- Government forms: Government agencies at the federal, state, and local level have stricter guidelines and regulations compared to many private sector businesses. From approving permits to clocking in on a timesheet, the signatures can streamline productivity by ensuring that the right employee is involved for the appropriate approvals.
- Shipping documents: For manufacturers, ensuring cargo manifests or bills of lading are always accurate helps reduce costly shipping errors. Yet, physical paperwork is cumbersome, isn’t always easily accessed in transit, and can be lost. By digitally signing shipping documents, shippers and receivers can access a file quickly, verify that the signature is up to date, and confirm that no tampering has occurred.
It’s important to choose a trusted CA, like Sectigo, for your digital signing and certificate needs. Learn about our document signing certificates today.