Don’t ‘Compromise’ Your Code Amid Malware Mayhem

Code Signing Certificates demand a price premium in the underground online marketplace. This is no surprise considering that criminals sometimes use them to dupe their potential victims into installing malware in their machine.
The code-signed malware appears safe to the users, whereas users receive an alert to be cautious if the malware is unsigned. In recent days, fraudsters have been injecting malware into popular remote conferencing software clients, such as Zoom, and many users are unaware that their devices are being compromised.
Dark web sellers sometimes stand up fake companies that may look like yours to untrained eyes and obtain this type of certificates from a Certificate Authority. In other cases, they steal them along with the sensitive private keys from an organization. Last year, hackers compromised the code signing certificate and the associated private key (which was not well protected) of Asus and infiltrated more than a million devices with malicious software. The danger is real.
It’s important to understand that Code Signing Certificates come in two flavors:
- The standard certificate requires a low-grade vetting of the requester of the certificate and his/her company information by the Certificate Authority that issues it. Keys are usually stored in software or the filesystem.
- The Extended Validation (EV) Code Signing Certificate requires a much higher degree of vetting by the Certificate Authority before it is issued. The keys are stored in well protected hardware.
Cyber criminals often opt for standard certs given the relative lower time and cost to obtain them.
In the case of EV Code Signing Certificates, the vetting process is mandated by the CA/Browser Forum, an industry consortium, and the requirements are strict to discourage the fraudsters from attempting to obtain an EV certificate. In fact, research from Georgia Tech’s Cyber Forensics Innovation Lab shows that EV SSL certificates are 99.99% likely to be free of phishing attacks and abuse. The data for EV Code Signing certificates may be similar. The research study, which was sponsored by Sectigo, can be downloaded here.
With more people spending time online due to COVID-19 lockdown, the number of malware attacks has significantly increased in recent days. If the rogue guys can use a Code Signing Certificate to make a malware appear legitimate, more people will fall for their scam. So, they might try to compromise your private key and the certificate.
To help protect you, an EV Code Signing Certificate requires that the key be stored in a high assurance, FIPS 140-2 or above standard-compliant hardware. There are USB tokens that meet this requirement and add another layer of protection with a PIN. Alternatively, you could store the key(s) in your organization’s Hardware Security Module (HSM) on-premise.
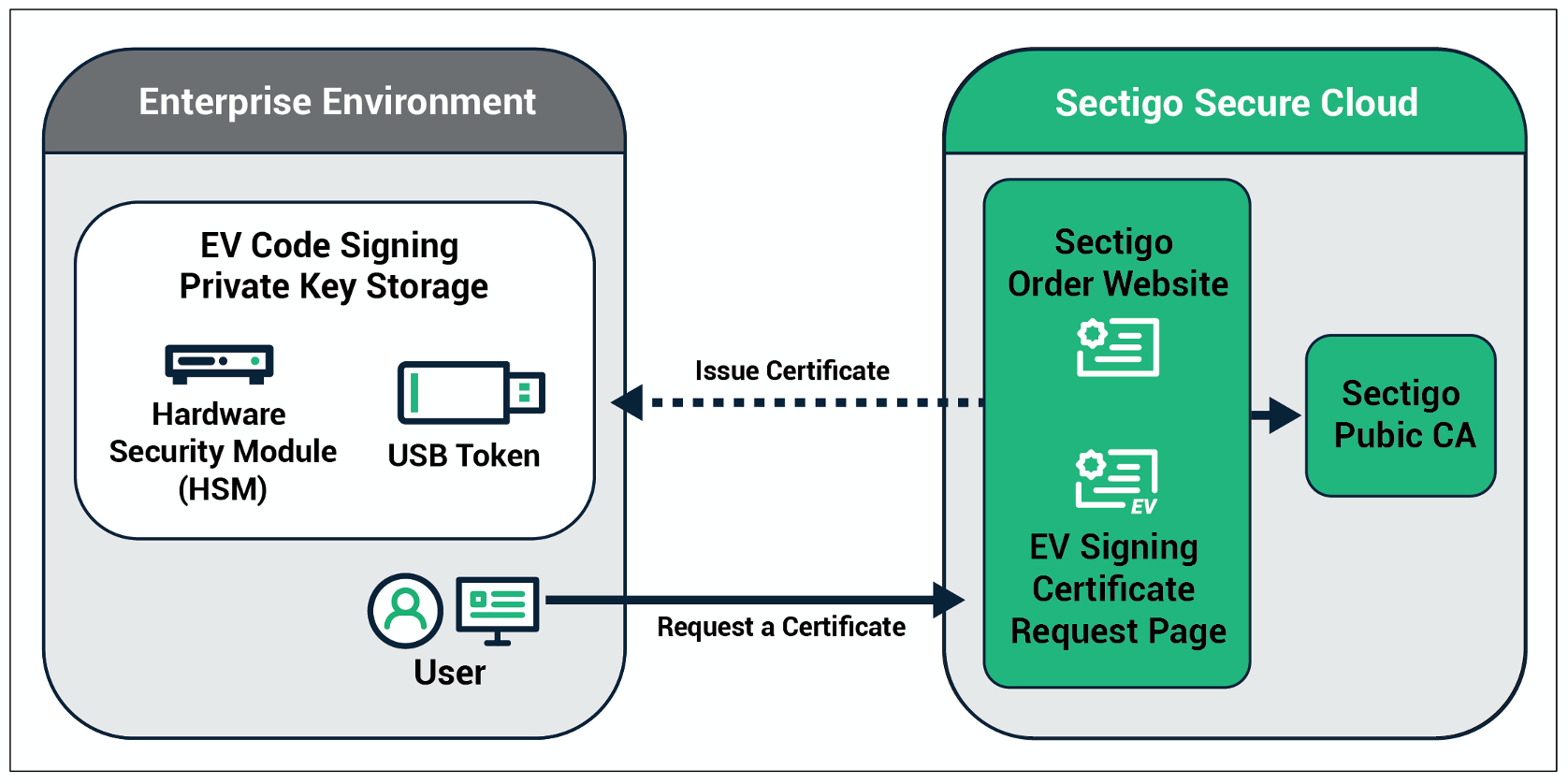
An EV Code Signing Certificate stores sensitive keys in well-protected hardware.
There are relative pros and cons for the above form factors. USB tokens provide individual allocation and assist with mobility. However, they could be misplaced or lost easily. HSMs help with centrally managing the keys typically safeguarding the hardware in a secure IT closet or data center, but these devices usually cost more. These elements have to be balanced with the organization’s needs to find an optimal solution.
Besides enhancing your security posture, an EV Code Signing Certificate enables:
- An instant reputation score with Microsoft’s SmartScreen Application Reputation filter. This means that you do not have to wait months so that your newly created application’s reputation is built up and your user base can trust it sooner.
- For Operating System kernel mode applications, Microsoft mandates that they be signed with an EV-grade Code Signing Certificate, essentially speeding up the ability to establish your software brand in the market.
Protect your private keys. Store them is FIPS compliant hardware. And, opt for an EV Code Signing Certificate, even if it means paying a little more money for it. The investment is worth it.
