-
Blog Post Apr 26, 2019
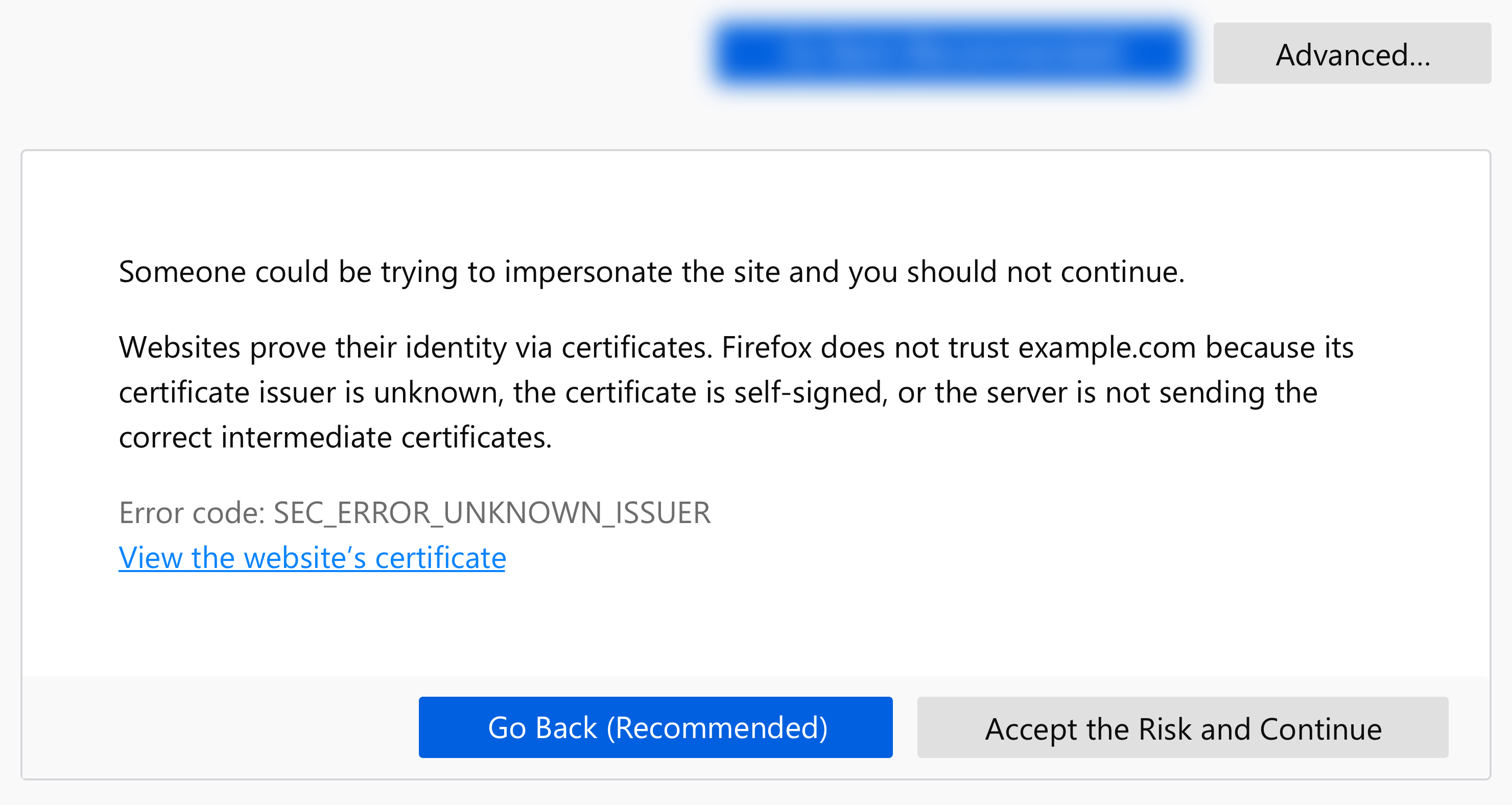
What the Latest Firefox Update Means for SSL Certificates
Learn what impacts the latest Firefox 66 update will have on your SSL certificates & what it means for your website security & user confidence.
-
Blog Post Apr 11, 2019
Should the EV-SSL-Enabled Interface Be Called a “Green Address Bar?”
When Extended Validation (EV) SSL first launched in 2007 people began to refer to the "green address bar." Browser interfaces have evolved since then. Perhaps the way we refer to how these TLS / SSL certificates display should evolve as well.
-
Learn More
Why Use Automated Certificate Management
Blog Post from Sectigo
 Blog Post Apr 04, 2019
Blog Post Apr 04, 2019Today, automated certificate management is essential. Use a Sectigo Proxy with Windows Active Directory server to issue both public & private certificates.
-
Blog Post Mar 28, 2019
Why Automation Matters to Enterprises Using S/MIME Email Certificates
It is tempting for the enterprise to use S/MIME without automated certificate management in hopes of saving some money by requiring employees to share the burden of managing certificates - but encryption and digital signatures are the best way to ensure the integrity and privacy of email communication. Using S/MIME for encryption allows both sender and recipient to utilize their existing S/MIME capable email applications with their familiar capabilities.
-
Blog Post Mar 26, 2019
Why CAs Charge More for Extended Validation SSL
Extended Validation (EV) SSL certificates are one of three standard SSL certificate types issued by Certificate Authorities: DV, OV, and EV. What makes EV certificates different from the others is that they provide the highest assurance that the domain is NOT associated with a bad actor. When users see a company-branded address bar next to the URL, they can know that they are on a trusted domain.
So is an EV SSL certificate right for you? In order to determine this, it’s important to understand why the cost is higher than other certificate options, the unique value it provides, and how the issuance process works.
-
Blog Post Mar 13, 2019
63-Bit Password Emphasizes Role of Automation in Enterprise PKI
Industry PKI experts recently have discovered a flaw in certificate generation practices that employ the commonly used EJBCA CA tool, which can result in serial numbers with 63 bits of entropy as opposed to the 64 bits required by public certificate guidelines. Episodes like this one put a spotlight on the value of automation in certificate practices. Automated capabilities enable the consistently correct maintenance, revocation, and replacement of a large number of certificates with little human interaction required.
-
Learn More
All Sectigo Public Certificates Meet 64-Bit Serial Number Requirements
Blog Post from Sectigo
 Blog Post Mar 13, 2019
Blog Post Mar 13, 2019Industry PKI experts recently have discovered a flaw in certificate generation practices that employ the commonly used EJBCA CA tool, which can result in serial numbers with 63 bits of entropy as opposed to the 64 bits required by public certificate guidelines. News reports indicate that several certificate issuers are affected. We would like to clarify that NO active public certificates from Sectigo are subject to this flaw.
-
Blog Post Mar 12, 2019
New Research Regarding Online Criminal Marketplaces for Certificates
A recent study by Georgia State University suggests that criminal online marketplaces feature a steady supply of TLS / SSL certificates from all major public CAs. Sectigo is eager to work with researchers like these and others to help reveal criminal activity and create strategies to mitigate its effectiveness without preventing legitimate business from benefiting from public certificates.
-
Learn More
Sectigo CIO Appointed to Rutgers Cybersecurity Program Advisory Board
Blog Post from Sectigo
 Blog Post Mar 11, 2019
Blog Post Mar 11, 2019Edward Giaquinto, our CIO, has been appointed Advisory Board Member at Rutgers University’s Cybersecurity Program. The Program is designed to train and develop professionals to manage cybersecurity issues within an organization, preparing them to analyze, manage and build cybersecurity competencies that can protect the organization.
-
Blog Post Mar 11, 2019
S/MIME 101: Making GDPR Compliance Easy with S/MIME
Since GDPR went into effect, encrypting email containing sensitive personal data has been widely considered a best practice of businesses operations. This should come as no surprise—email in Europe carries the same vulnerabilities as email in the U.S., and unencrypted email is readable by a number of different parties, including the enterprise IT administrator, the internet service provider, and the cloud service mail provider.
-
Blog Post Mar 04, 2019
S/MIME 101: Maintaining DFARS Compliance Using S/MIME
Supplementing the original Defense Federal Acquisition Regulation to mandate encryption of all data at rest or in transit, DFARS creates a security baseline that must be met by all contractors. Since email is just as indispensable to defense contractors as it is to any other industry, this means that effective encryption tools must be set in place before doing business with the government.
-
Blog Post Mar 01, 2019
Authentication Is Not for the Party Being Authenticated
Many people would be surprised to learn that the purpose of digital certificates is not to enable encryption. Our IT systems are frequently engineered not to enable encryption unless certificates are in place (most obviously when connecting to a web site using a popular desktop or mobile browser), but that decision is in recognition of the original purpose of certificates, which is to authenticate the identity of a participant in a digital transaction.