-
Learn More
Prevent Revenue Loss from the New One-Year SSL Term Limit
Blog Post from Sectigo
 Blog Post Feb 21, 2020
Blog Post Feb 21, 2020Apple recently announced its upcoming distrust for two year SSL certificates.
Sectigo understands the benefits of and supports shorter certificate lifetimes. We also know that the currently imposed two-year limitation has already impacted our SSL certificate resellers by causing user friction, reducing Average Sales Prices (ASPs), and negatively affecting overall revenue. This new industry standard will further impact revenue for our partners.
-
Blog Post Feb 18, 2020
We Are Sectigo | Surup Desai
“My job is to predict the future,” says Sectigo Director of Financial Planning & Analysis Surup Desai. “ Surup describes how he looks after financial, sales, and revenue operations at the company, and—no matter which hat he is wearing—he is always cognizant of how his work fits into Sectigo’s overall vision.
-
Blog Post Feb 18, 2020
How to Keep Hackers Away from Tomorrow’s Smart Cities
Everything in our cities is connected; traffic controls, vehicles, and buildings—to the point that cities are smart enough to adapt to human needs and are engineered to function at the highest possible levels of power efficiency and effectiveness. But with this connectivity come dangerous vulnerabilities.
-
Blog Post Feb 18, 2020
We Are Sectigo | Vince Chiu
No one loves an extraordinary transformation more than Vince Chiu, Sectigo’s Marketing Operations Manager. Vince, a cybersecurity industry expert with considerable experience in the SSL space, joined Sectigo in 2018, timed with the company’s brand transition. From setting and meeting aggressive KPIs to helping with brand strategy, Vince and his team have brought new energy to the marketing department, finding exciting ways to leverage data to build better solutions.
-
Blog Post Jan 22, 2020
NamesCon Global 2020 & Sectigo
Sectigo and I are excited to be attending NamesCon Global and sharing some industry-changing product news. We are changing the way our partners and the world should be thinking about SSL - creating differentiation that we can’t wait to share. We'll begin sneak peek conversations in Austin, and invite our partners and prospects to be the first to know the inside scoop.
-
Learn More
Sectigo Code Signing Authentication Evolves
Blog Post from Sectigo
 Blog Post Jan 07, 2020
Blog Post Jan 07, 2020Some Sectigo Code Signing certificate subscribers have opined recently that our Code Signing authentication now includes additional steps and requirements it did not have in previous years. This observation is accurate. Sectigo of recent has increased its process and requirements for obtaining Code Signing certificates.
-
Blog Post Dec 18, 2019
Sectigo Executives Share 2020 Predictions
Turning attention to 2020, our leadership team has been working to identify predictions about quantum computing, automation, IoT security, and legislation.
-
Blog Post Dec 04, 2019
Five Ways PKI Protects and Secures Financial Services Data
Data has become the lifeblood of the financial services industry. From managing transaction details and providing real-time account and trading information to automating risk management processes, forecasting, and fraud detection, data is integral and the most important resource to protect.
-
Blog Post Nov 26, 2019
On Black Friday and Cyber Monday, Look Out for “Not Secure” Warnings
As millions of people visit online retailers to spend their hard-earned money this holiday, cybercriminals will be working to trick consumers into mistakenly sending that money their way, instead. A number of browsers are pioneering new ways for users to recognize that the site they are visiting might not be what it appears. Non-HTTPS pages, or pages without an EV SSL certificate validating them as trustworthy, will be flagged as potentially dangerous sites.
-
Learn More
How Let's Encrypt Runs CT Logs
Blog Post from Sectigo
 Blog Post Nov 25, 2019
Blog Post Nov 25, 2019[This guest post originally ran on Let’s Encrypt’s blog on Nov 20, 2019.] Let’s Encrypt launched a Certificate Transparency (CT) log this past spring. We’re excited to share how we built it in hopes that others can learn from what we did. . . Sectigo and Amazon Web Services generously provided support to cover a significant portion of the cost of running our CT log.
-
Blog Post Nov 20, 2019
Australia's IoT Cybersecurity Guidelines for Embedded Device Security
Australia has joined the ever-swelling ranks of government and industry organizations developing guidelines or enacting regulations regarding IoT device security. On Nov. 11, 2019, the country published their “Draft Code of Practice: Securing the Internet of Things for Consumers,” which outlines 13 security practices intended to apply to all IoT devices available in Australia.
-
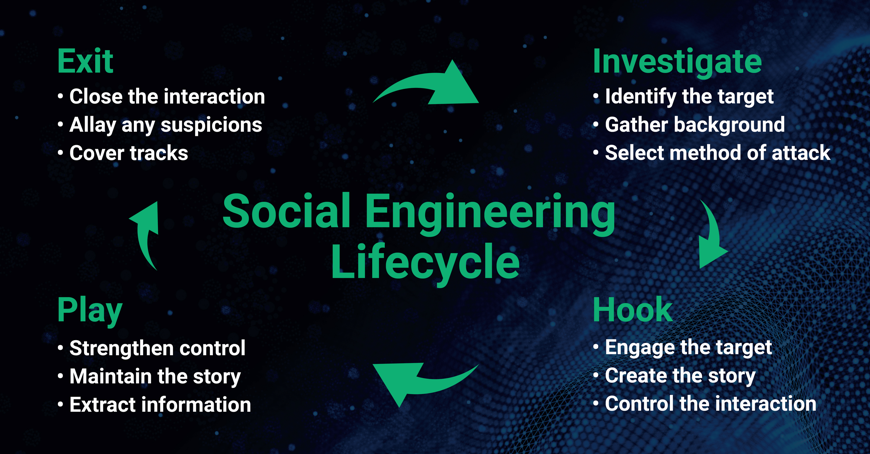
Blog Post Nov 05, 2019
Social Engineering: Friend or Foe?
In a social engineering attack, a bad actor uses human interaction (social skills) to acquire information about a company and/or its computer systems. Attackers often seem unassuming and respectable, often claiming to be a new employee, a service technician, or a member of the service-providing company and may even offer credentials to support that identity.