Australia's IoT Cybersecurity Guidelines Highlight Importance of Embedded Device Security

Australia has joined the ever-swelling ranks of government and industry organizations developing guidelines or enacting regulations regarding IoT device security. On Nov. 11, 2019, the country published their “Draft Code of Practice: Securing the Internet of Things for Consumers,” which outlines 13 security practices intended to apply to all IoT devices available in Australia.
While Australia’s initiative is not unique, it illustrates the growing realization that companies can no longer ignore the need to secure IoT devices. The Australian Initiative, at least for now, is voluntary. Other governments are taking this further, passing laws requiring minimal levels of security and it is not unreasonable to think that Australia will eventually follow suit.
Regardless of the legal status, this raises the stakes for OEMs building IoT devices.
IoT Security Principles
The 13 principles outlined in the document, while perhaps not comprehensive enough, provide a strong foundation for security of IoT devices. While some of the items relate to providing consumers with control over their personal data and ensuring consumers can actually help manage the security of their devices, most are aimed at increasing the security of IoT devices. These include:
- No default or weak passwords
- Secure software updates
- Secure key storage
- Encryption of data at rest and data in motion
- Minimizing attack surfaces
- Secure communication
- Secure boot
These requirements map into the IoT Identity and Integrity solutions provided by Sectigo.
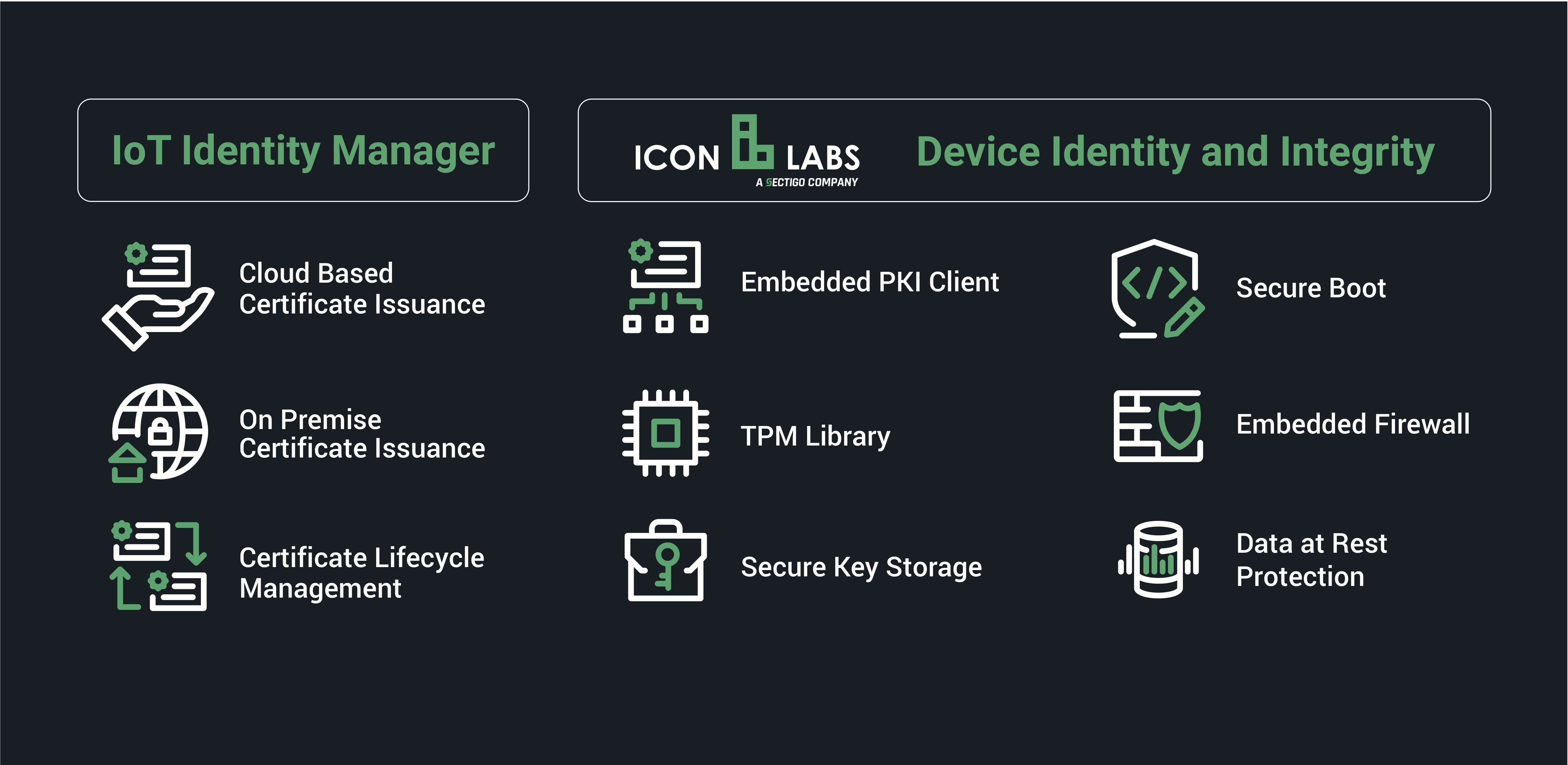
A security framework, such as Sectigo’s IoT Identity and Integrity Suite, provides an integrated suite of security building blocks, and provides a foundation for compliance with a wide range of existing and emerging security guidelines and standards.
IoT Security Implementations
The Australian Cybersecurity guidelines highlight the importance of building security into IoT devices. This requires security features that protect the device from attack, protect the integrity of the device, and enable device identity. Sectigo’s IoT authentication and integrity solutions provides IIoT and IoT OEMS with best-in-breed solutions for authenticating and securing connected devices, including:
- Secure Boot.Provides embedded software APIs that ensure software has not been tampered with from the initial “power on” to application execution. Secure Boot also lets developers securely code sign-boot loaders, microkernels, operating systems, application code, and data.
- Device Identity Certificates. Adding digital certificates to devices during manufacturing ensures that devices are authenticated when they are installed on a network, as well as before communicating with other devices in the network—protecting against counterfeit devices being introduced into the network.
- Embedded Firewalls. By working with real time operating systems (RTOS) and Linux to configure and enforce filtering rules, embedded firewalls prevent communication with unauthorized devices and blocking malicious messages.
- Secure Elements. OEMs and medical device manufacturers should use secure elements, such as a trusted platform module (TPM) compliant secure element, or an embedded secure element for secure key storage. Secure key storage enables secure boot and PKI enrollment using key pairs generated within the secure element, providing very high levels of protection from attacks.
- Secure Remote Updates. It’s important to validate that device firmware has not been modified before installation. Secure remote updates ensure components are not modified by bad actors and are authenticated modules from the OEM.
Keeping IoT devices and information safeguarded from cyberattack is not simple and will never be perfect. It’s an ongoing battle. Cyber criminals are always improving their methods and developing new, clever attack tactics. However, staying current with cybersecurity best-practices and using proven security solutions, including those outlined in the Australian Cybersecurity Guidelines, provides a strong foundation for protecting devices from cyberattacks.
