Apple proposes 47-day SSL/TLS certificate lifespans by 2029. What this means for your business
*This blog article was updated on 04.14.2025 based on ballot vote on 11/04/2025 that confirmed the new certificate lifespan.
On October 9, 2024 during the second day of the fall CA/Browser Forum face-to-face meeting, Apple revealed a draft ballot for discussion on GitHub, proposing an incremental reduction of maximum term for public SSL/TLS certificates. On April 11, 2025, Apple’s proposed ballot - sponsored by Sectigo - passed with no votes against it.
This phased approach will reduce certificate lifespans over the course of the next four years to 47 days by 2029, and also includes a gradual reduction of the domain control validation (DCV) reuse period, eventually requiring revalidation every 10 days.
Table of Contents
An accelerating trend of shortening digital certificate lifespans
This move from Apple follows Google’s previous announcement in its “Moving Forward, Together” roadmap of its intention to reduce the maximum validity for public SSL/TLS certificates from 398 days to 90 days, in a future policy update or a CA/B Forum ballot proposal.
The current Apple ballot passing and Google’s 90-day proposal clearly sends a strong message to the industry with the two largest browsers both advocating for shorter digital certificate lifespans.
In this new era of certificate lifespans, here’s what businesses can expect:
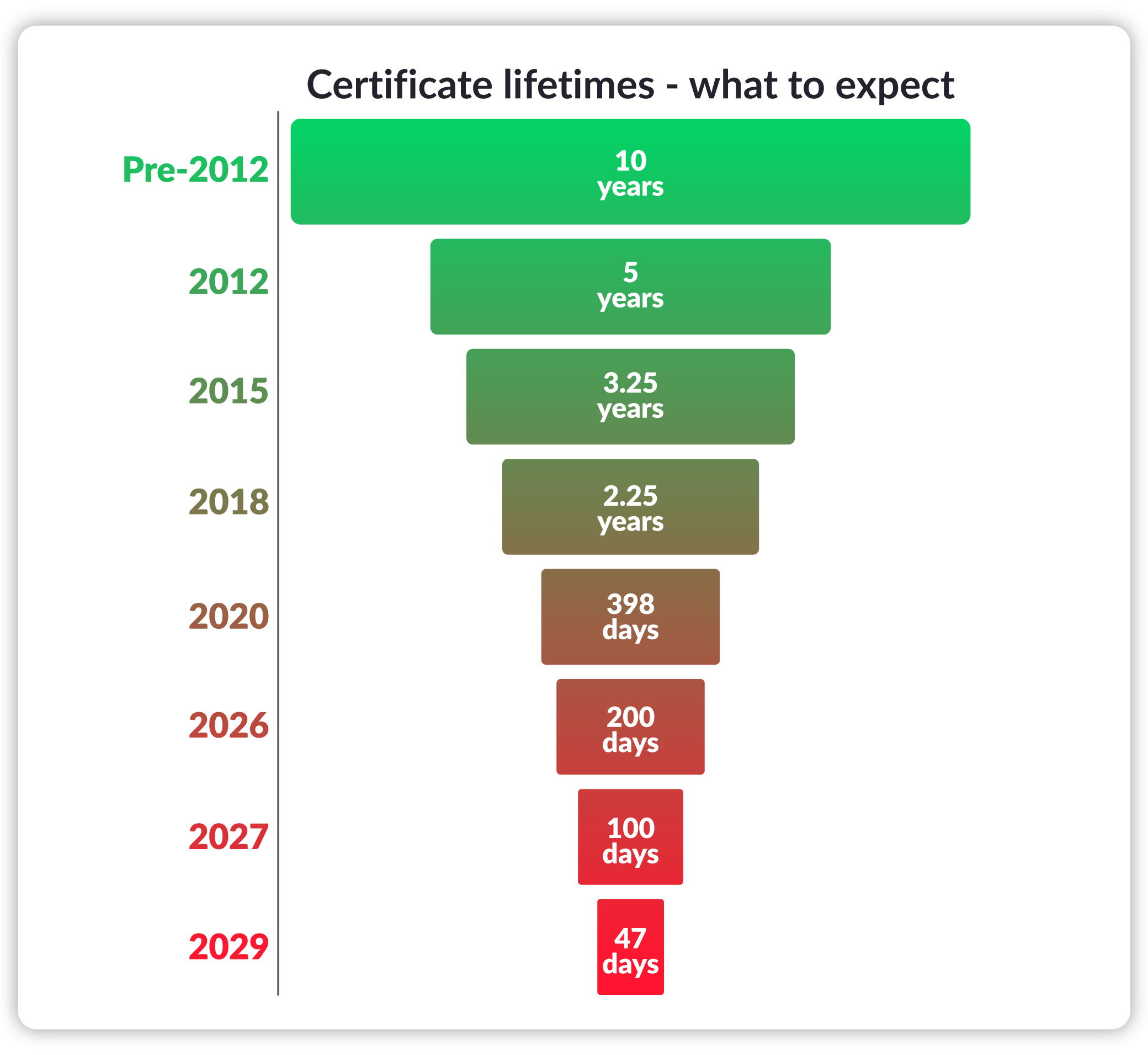
Chart of certificates lifetimes expectations
Why are these numbers what they are?
The public certificate lifespans proposed by Apple may seem complex at first, but they follow a simple logic of ideal certificate term + early renewal window:
- 200 days = 180 days (6 months) + 20 days early renewal
- 100 days = 90 days (3 months) + 10 days early renewal
- 47 days = 42 days (6 weeks) + 5 days early renewal
But although there’s logic behind this, the gradual decrease in certificate lifespans will no doubt prove a headache for busy IT security teams, juggling with lots of certificates expiring at different times. It’s easy to predict that companies that use manual methods for tracking and monitoring certificate expiries will soon find themselves overwhelmed by the rapidly changing certificate lifespans. After all, what Apple is suggesting is that certificate lifecycles now change every year!
In addition to the reduction in maximum certificate terms, the DCV reuse period is also going to decrease as follows, if the proposal passes:
Date | Maximum certificate term | DCV reuse period |
3/15/26 | 200 days | 200 days |
3/15/27 | 100 days | 100 days |
3/15/28 | 100 days | 10 days |
3/15/29 | 47 days | 10 days |
It's time to automate certificate lifecycle management
This proposal highlights the critical importance for businesses of all sizes to seriously consider and implement fully automated certificate lifecycle management (CLM). There’s real urgency for organizations to adopt a “set it and forget it” approach to certificate renewals, so any future change in renewal windows don’t impact their operations or cause unnecessary downtime and outages.
Sectigo is fully committed to supporting these initiatives from the browsers. Our decision to sponsor this latest ballot proposal is a testament to our dedication towards the integrity of the WebPKI ecosystem and the security of our customers. Sectigo Certificate Manager (SCM) is the most comprehensive certificate lifecycle management platform on the market, designed to proactively address the SSL challenges of tomorrow. Schedule a demo today to learn how your company can benefit from SCM, or start a free trial.
Want to learn more? Get in touch to book a demo of Sectigo Certificate Manager!
Related posts:
The evolving SSL/TLS certificate lifecycle & how to manage the changes
How to renew SSL certificates & how to automate the process
Why SSL certificates expire: exploring the benefits of shorter validity periods
