Preparing for the future: Apple’s 47-Day certificate lifespan proposal


The digital certificate lifecycle is undergoing significant changes, with a push towards shorter validity periods for SSL/TLS certificates. Currently, the lifespan of certificates is about 398 days, but companies like Google and Apple are advocating for much shorter terms, with Apple proposing to reduce lifespans to just 47 days by 2029. This shift aims to enhance security by limiting the time a compromised key can be exploited, but it poses challenges for IT teams accustomed to longer renewal periods. Organizations must prepare for this transition by adopting automated certificate management solutions to manage the increased administrative burden effectively.
Article updated on 10th March, 2025 due to latest Apple announcement.
The digital certificate lifecycle provides a structured process through which digital certificate are used for communications over Secure Socket Layer (SSL) / Transport Layer Security (TLS). Certificates are validated, issued, deployed, and eventually renewed (or revoked). Despite its apparent stability, however, this lifecycle is constantly in flux. It has undergone significant changes through the years — including a continual effort to reduce the total lifespan.
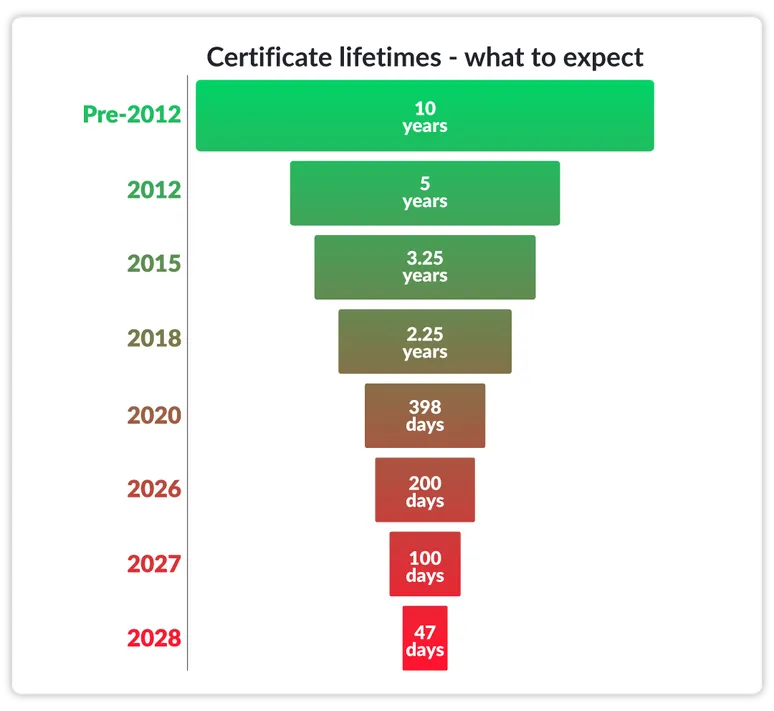
While the current lifespan typically extends 398 days, it is increasingly evident that this will not be the status quo for much longer. Much discussion has surrounded Google's stated intention to shift to 90-day certificates, but Apple is eager to take things a step further, with even shorter lifespans. Apple's goal: to reduce validity periods to a mere 47 days by 2029.
Announced during a Certification Authority Browser Forum (CA/B Forum) meeting, Apple submitted a draft ballot, featuring a proposal to incrementally reduce terms for SSL/TLS certificates until they reach just 47 days. Sponsored by Sectigo, this proposal integrates specific certificate terms and early renewal windows while also limiting Domain Control Validation (DCV) reuse periods. We will break down the proposal below, highlighting key dates along with next steps for preparing for the new normal in the digital ecosystem.
Key dates during the push to 47-day validity periods
Apple's proposed shift to 47-day SSL validity periods could occur over the course of a few years, with several milestones provided along the way. We will discuss important dates in detail later on but for now, one especially critical date should be top of mid-to-late 2029. This is when 47-day certificate lifespans could take over.
Remember: for the time being, this remains a proposal. It must be voted in to ensure that 47-day terms are actually implemented. Still, this proposal reflects the industry's clear shift towards shorter certificate lifespans. Even if Apple does not adopt the 47-day proposal, it is likely that limited lifespans will enter the picture in some capacity.
Current SSL certificate lifespan
Allowing for over a year of usage prior to renewal, the current SSL certificate lifespan typically extends a comparatively lengthy 398 days. Despite this, many enterprises struggle to keep up with certificate renewals, suffering a significant risk of outages as a result. Still, the current 398-day lifespan allows for something of a buffer, which will no longer be available if Google's 90-day or Apple's 47-day intentions are realized.
Timeline for certificate lifespan reductions
In addition to signaling the intention to move to shorter validity periods, Apple has created a clear roadmap revealing how this process will play out. Rather than immediately shifting to 47-day lifespans, Apple would follow a gradual process, with lifespans shrinking at a slower and steadier pace.
Before outlining key milestones along the way, it's important to mention: a fundamental process involving the public key infrastructure (PKI) could play heavily into Apple's plans for reducing certificate lifespan. Known as Domain Control Validation (DCV), this involves the Certificate Authority's verification of the requestor's domain. This is a crucial component of the SSL/TLS process; without DCV, certificates cannot be issued or deployed. DCV reuse, however, makes it possible to skip revalidation under certain circumstances.
With that in mind, businesses and enterprises planning for the possible shift to 47-day lifespans will want to be cognizant of these key dates:
September, 15th, 2025. If Apple's proposal is adopted, the certificate lifespan will shrink to a total of 200 days. The term for early renewal, however, will extend just 20 days. At this point, the DCV reuse period will span 200 days.
September 16th, 2026. Following a year of 200-day lifespans, Apple will take the next step in its journey, adopting a 100-day lifespan along with 10 days allocated for early renewal. Meanwhile, the DCV reuse period will also shrink, reaching 100 days.
Mid-to-late September 2029 could bring a crucial change to Apple’s 47-day certificate lifespan plan, reducing the Domain Control Validation (DCV) reuse period to just 10 days.
Implications of Apple’s 47-day proposal
Apple's proposal is indicative of a major trend in the cybersecurity space, where shorter certificates are viewed as crucial for addressing a wide range of security risks. In the event that a private key is compromised, a shorter lifespan limits the bad actor's ability to actually exploit that key. Unfortunately, these security benefits can be difficult to leverage when organizations are constantly scrambling to keep up with the fast pace of renewal. If the 47-day proposal becomes a reality, organizations will need to upgrade to automated certificate management strategies.
Security benefits
With each additional day, week, or month, certificates show greater potential to be compromised by increasingly sophisticated threat actors. In the worst-case scenario, attackers should have limited time available to misuse compromised certificates. Short validity periods also encourage strong compliance and agility.
Operational burden on IT teams
For all their benefits, short certificate lifespans pose significant problems from the perspective of already busy IT professionals. Many are overwhelmed by the sheer volume of digital certificates, especially if they remain committed to time-consuming manual processes. Without a streamlined, automated process in place, the increased need for renewals could strain already
Concerns and challenges
Challenges are to be expected as certificate lifespans continue to shrink. While organizations will ultimately benefit from the enhanced security that these shorter lifespans enable, they must first overcome a few roadblocks:
Legacy systems and non-automated environments
Although automation is strongly encouraged even when dealing with longer, 397-day lifespans, some organizations have previously managed to get by with manual renewal strategies. This certainly places a burden on IT departments — and it can lead to significantly higher labor costs and increased risks of human error — but this approach was at least somewhat viable with longer lifespans. That is all about to change, however, and organizations will need to adjust rapidly to new systems as they embrace automation.
Another concern: legacy systems frequently lack compatibility with the Automated Certificate Management Environment (ACME). These systems may be more vulnerable to certificate expiration and may also struggle with limited scalability.
Strain on small businesses and resource-constrained organizations
While the challenges described above could easily strike organizations of all sizes and within many sectors, these issues could prove especially problematic for smaller businesses — which may already experience strain in their IT department. Without automation built into the certificate management process, smaller organizations risk outages and with them, a wide range of security issues that they may be ill-equipped to address.
Preparing for 47-day certificate lifecycles: the role of automation
At this point, shorter certificate lifespans are not a matter of if, but when. Organizations that fail to prepare accordingly could be in for a world of trouble when reduced lifespans inevitably emerge. Depending on current strategies, this effort may involve a shift to automated certificate management.
Importance of automated certificate lifecycle management
Automation has a powerful role to play in addressing the expanded administrative and IT burdens associated with short SSL certificate lifespans. Automated Certificate lifecycle management (CLM) solutions, in particular, promise to streamline difficult processes, offering an efficient alternative to the manual processes of yesteryear. ACME allows for automated renewal, but end-to-end certificate lifecycle management is crucial — especially for the enterprise environments of tomorrow.
Preparing your infrastructure
Some prep work may be needed prior to upgrading certificate management solutions. First, determine whether current systems support ACME and other automation tools. Start planning for infrastructure upgrades well in advance, as these can be time-consuming to implement.

Steps to take now
While the key dates highlighted above may seem far away, the switch to automated solutions can take time. It's important to start planning and implementing strategies now to ease the inevitable transition to shorter certificate lifespans. In addition to evaluating and upgrading infrastructure, follow these steps to improve readiness for reduced certificate validity periods:
Immediate actions
In this evolving digital environment, it is abundantly clear that automated certificate management is a must. The goal: to reduce manual tasks and adjust to automated workflows. If automation is not yet part of the process, now is the time to begin evaluating CLM solutions and determining how they fit into the bigger picture of enterprise security. If automation is already in place, additional action may still be required: auditing current systems to ensure that they can meet the increased demands brought about by shorter validity periods.
Long-term planning
As you take immediate steps towards accommodating limited certificate lifespans, be mindful of strategic planning. This can determine how certificate management will be handled not only in the midst of immediate changes, but also, far into the future. Strong planning should enhance scalability and agility while also boosting the ROI associated with automated certificate management.
Start preparing now for shorter certificate validity periods with Sectigo
Whether first brought about by Google or Apple, it's clear that shorter certificate validity periods are in the works. Now is the time to prepare, so that the inevitable shift towards shorter lifespans does not create an administrative nightmare. Sectigo can provide powerful guidance to help ease this transition.
Sectigo Certificate Manager (SCM) automates the entire SSL certificate lifecycle from issuance and discovery to deployment and renewal handling large volumes of SSL/TLS certificates with ease. With SCM's centralized dashboard, you gain real-time visibility into all your certificates, eliminating manual workloads and minimizing the risk of unexpected expirations.
Prepare for the future of certificate lifecycle management today by experiencing our SCM Platform in action, request a demo or start a free trial.
