Public and private keys in public key cryptography


Public key infrastructure (PKI) is used to manage identity and security in internet communications. As the core technology enabling PKI, public key cryptography is an encryption mechanism that relies upon the use of two related keys, a public key and a private key. These two keys are used together to encrypt and decrypt a message. Pairing two cryptographic keys in this manner is also known as asymmetric cryptography. Public key cryptography uses cryptographic algorithms to protect identities and data from unauthorized access or use, guarding against attacks from cybercriminals and other malicious actors.
How public key cryptography works
The public key is comprised of a string of random numbers and can be used to encrypt a message. Only the intended recipient can decipher and read the message by using the corresponding private key, which is also made up of a long string of random numbers. This private key is a secret key, and must remain known only to the recipient. The pair of keys are mathematically related so that whatever is encrypted with a public or private key can only be decrypted by its corresponding counterpart.
Public key cryptography benefits
The primary benefit of public key cryptography is increased data and identity security at scale. What makes the process secure is that the private key is kept secret by its owner, and no one is ever required to reveal or share a private key.
While it may seem counterintuitive, using a key pair consisting of two private keys for encrypting and decrypting sensitive information is not more secure than asymmetric cryptography. Using symmetric key algorithms, with two private keys, requires that both parties in the communication have access to the secret keys, increasing the risk as both now need to keep the secret. Additionally, symmetric key algorithms cannot easily scale as it is nearly impossible to coordinate the vast number of connections necessary to privately share all necessary combinations of private keys.
The public key cryptography architecture is so scalable that it is able to secure billions of messages exchanged daily by organizations over their own networks and across the internet. What enables this is that public keys can be distributed widely and openly without malicious actors being able to discover the private key required to decrypt the message.
The difference between public keys vs private keys
In short, the main difference between a public key and a private key is that one encrypts while the other decrypts. In public key cryptography, an encryption key (which could be the public or private key) is used to encrypt a plain text message and convert it into an encoded format known as cipher text. Then the other key is used as a decryption key to decrypt this cipher text so that the recipient can read the original message.
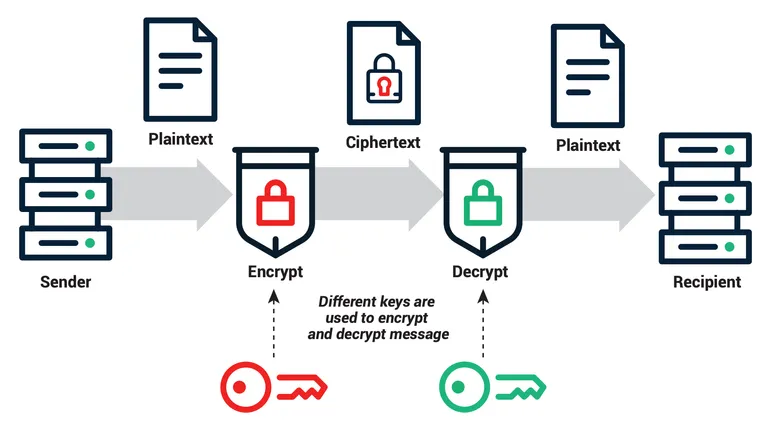
How the public key works
What is a public key? The public key is published for all the world to see. They are created using a complex asymmetric algorithm to pair them with an associated private key. The most common algorithms used to generate public keys are:
- Rivest–Shamir–Adleman (RSA)
- Elliptic curve cryptography (ECC)
- Digital signature algorithm (DSA)
These algorithms use various computation methods to generate random numeric combinations of varying length so that they cannot be exploited with a brute force attack. The key size or bit length of public keys determines the strength of protection. For example, 2048-bit RSA keys are often employed in SSL certificates, digital signatures, and other digital certificates. This key length offers sufficient cryptographic security to keep hackers from cracking the algorithm. Standards organizations like the CA/Browser Forum define baseline requirements for supported key sizes.
How the private key works
What is a private key? Unlike the publicly accessible public key, the private key is a secret key known only by its owner. When the two are paired, the recipient can use the corresponding key to decrypt the cipher text and read the original message. Private keys are generated using the same algorithms that create their public counterparts to create strong keys that are bonded mathematically.
Using public key pairs to ensure both security and identity
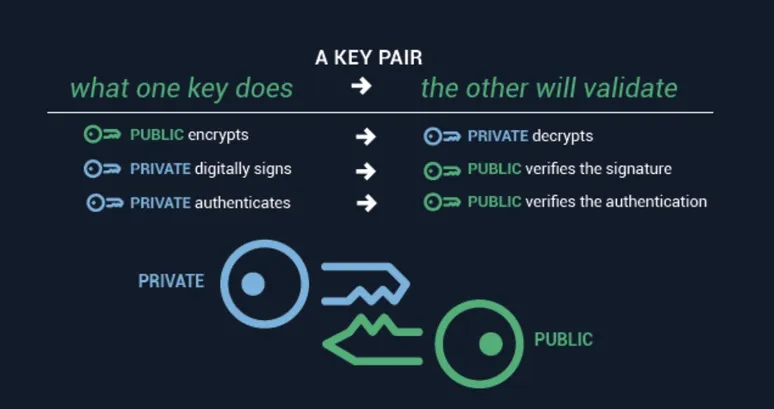
One of the unique advantages of asymmetric encryption using public key pairs is the ability to ensure both the security of encrypted messages and the identity of the sender. When looking to ensure security of messages, the sender looks up the recipient's public key and uses it to encrypt the message. The message can be transmitted openly over the Internet, and since only the recipient can decrypt the message with the appropriate private key, secure transmission is ensured.
The order of using the key pairs can also flip to ensure the identity of the sender. If a sender uses a private key to encrypt a message, the recipient can use the sender's public key to decrypt and read it. Since anyone can decrypt the message with the sender's public key, the message transmission is not necessarily secure, but since the private key is known only to the sender, the message is guaranteed to have come from that machine.
Common applications of public key cryptography
Many protocols rely on asymmetric cryptography. There are many applications of the technology, including web server security, digital signatures, document signing, and digital identities.
Web server security
Public key cryptography is the basis for the secure sockets layer (SSL) and transport layer security (TLS) protocols that are the foundation of HTTPS secure browser connections. Without SSL/TLS certificates to establish secure connections, cybercriminals could exploit the Internet or other IP networks using a variety of attack vectors, such as man-in-the-middle attacks, to intercept messages and access their contents. Public key cryptography serves as a sort of digital fingerprint verification to authenticate the recipient’s and sender’s identities and can thwart man-in-the-middle attacks.
Digital signatures and document signing
In addition to being used to encrypt messages, key pairs can be used for digital signatures and document signing. Public key cryptography uses the sender's private key to verify a digital identity. This cryptographic verification mathematically binds the signature to the original message to ensure that it has not been altered.
Digital identities
Public and private key pairs also provide effective identity authentication. As data and applications expand beyond traditional networks to mobile devices, public clouds, private clouds, and Internet of Things devices, securing identities becomes more important than ever. And digital identities don't have to be restricted to devices; they can also be used to authenticate people, data, or applications. Digital identity certificates using asymmetric cryptography enable organizations to improve cybersecurity by replacing passwords, which attackers have become increasingly adept at stealing.
Other applications of public key cryptography include S/MIME certificates, which validate email senders and encrypt email contents to protect against spear phishing attacks and SSH keys to control employee access to servers.
The role of certificate authorities in public key cryptography
A critical component enabling public key cryptography is a trusted agent to publish the public keys associated with individuals' private keys. Without this trusted authority, it would be impossible for senders to know they are in fact using the correct public key associated with the recipient's private key, and not the key of a malicious actor intending to intercept sensitive information and use it for nefarious purposes.
These trusted agents are known as certificate authorities (CAs). Trusted, third-party organizations like Sectigo act as private certificate authorities, but many enterprises and technology providers also choose to act as their own CAs. Either way, the certificate authority must be trusted to check and vouch for the identity of all senders whose public keys they publish, ensure that those public keys are indeed associated with the private keys of the senders, and safeguard the levels of information security within their own organization to guard against malicious attack.